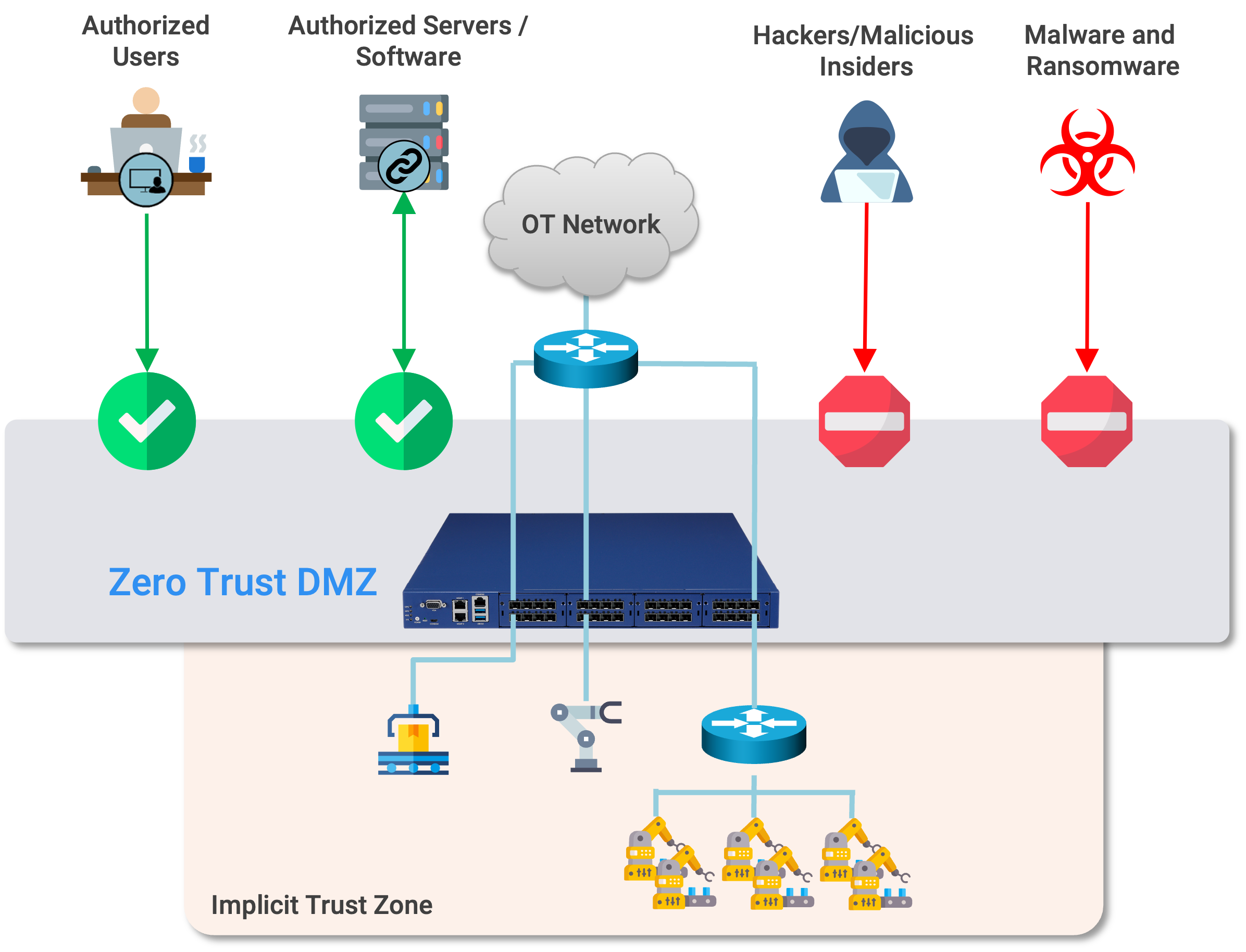
Zero Trust is a Journey

There's been a recent groundswell of support for the Zero Trust movement, with NIST SP 800-207 formalizing the definition of a Zero Trust Architecture, and other agencies such as the NSA releasing guidance to promote the trend. Zero Trust has absolutely hit the primetime. And as this Google Trends query shows, the public is responding – interest in Zero Trust keeps hitting new highs.
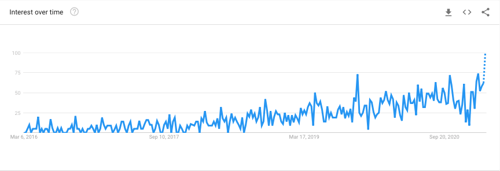
Fig 1: Google Trends query for "zero trust" (March 2021)
With all of the news out there on Zero Trust, it's easy to think of it as a "magic bullet" that will solve all cybersecurity problems. The truth is, it can be, but only when companies carefully set up and manage Zero Trust access policies. And that's where the trouble starts.
As one of the early pioneers in this field, we've helped many companies make the transition to Zero Trust, and have learned through the experience. Here are some of the lessons we learned.
DO: Get executive sponsors to drive Zero Trust transformation.
Institutional knowledge is usually a good thing – as people get better and better at solving one type of problem, they become more efficient. But let's face it. Most of the time, despite their best intentions, these same people tend to get in the way of change initiatives. New initiatives are, well... new, after all. They change processes and procedures, require learning new technologies, and generally create confusion and resistance.
The best way to solve these problems is to start with executive buy-in. Top executives can change the atmosphere overnight by lending their imprimatur, rallying support to the Zero Trust initiative and cutting through unnecessary red tape.
The good news is, because of the increasing awareness of and support for Zero Trust, it's becoming easier and easier to educate the top brass. The question they're increasingly asking is, "Why aren't we already doing this?"
DON'T: Boil the ocean.
 OK, so your CEO just read about this new "Zero Trust" thing and now wants to know when the company will be immune from all ransomware and cyber threats? (cue the Mission Impossible theme music)
OK, so your CEO just read about this new "Zero Trust" thing and now wants to know when the company will be immune from all ransomware and cyber threats? (cue the Mission Impossible theme music)
In our experience, it can be a mistake to treat Zero Trust adoption as a singular event. Trying to plan for every user and every project in every datacenter and cloud to become Zero Trust is be a recipe for failure. Most often, it leads to long delays, infighting, and missed opportunities. This is not the kind of transformation that calls for "ripping off the Band-Aid."
DO: Set reasonable expectations, and prioritize! Create a plan for Zero Trust adoption, starting with a few simpler proof-of-concept applications, aiming for "quick wins" that can establish trust in the transformation process and help you establish transformational patterns that can help accelerate the process.
Create a plan for Zero Trust adoption, starting with a few simpler proof-of-concept applications, aiming for "quick wins" that can establish trust in the transformation process and help you establish transformational patterns that can help accelerate the process.
Once processes and procedures are set, start migrating applications, with applications and data that have critical value and need to be protected – enabling cloud applications to reach on-prem services, establishing remote vendor access to the machines on the manufacturing floor, or segmenting the HR database, for example.
DO: Leverage your existing infrastructure. Zero Trust tools from different vendors vary widely in their implementation and deployment models. Some approaches, for example, require significant investment (both time and money) to overhaul existing networking and security equipment just to get them "Zero Trust-Ready." Such approaches are only partial solutions – they may work in the on-prem environment, or in certain sites, but won't help in the cloud or next generation edge environments that you'll need to support soon. It's not
Zero Trust tools from different vendors vary widely in their implementation and deployment models. Some approaches, for example, require significant investment (both time and money) to overhaul existing networking and security equipment just to get them "Zero Trust-Ready." Such approaches are only partial solutions – they may work in the on-prem environment, or in certain sites, but won't help in the cloud or next generation edge environments that you'll need to support soon. It's not
Instead, look for solutions that can deliver on top of your existing network. This lets you focus on what's important – Zero Trust – not bringing up a whole new network.
DO: Adopt a "kaizen-style," growth-oriented approach to Zero Trust. Kaizen is the Japanese concept of continuous improvement, popularized through its application to mass production to reduce waste and improve quality and efficiency.
Kaizen is the Japanese concept of continuous improvement, popularized through its application to mass production to reduce waste and improve quality and efficiency.
How does this apply to Zero Trust?
For all but the most simple access cases, getting the policies right may take some tuning. You'll probably want to start with relaxed security policies to minimize potential impact to business productivity. Locking out the CEO on day 1 isn't a good way to get the project off the ground. And it's fairly safe to assume that your Zero Trust solution has a lot of security knobs – maybe more than you're ready to use at the outset, anyway.
Make sure your Zero Trust solution can give you feedback that you can use to guide the process. For example, Zero Trust tools that help you map and measure the size of your attack surface can give you interactive feedback about which policy changes have the biggest impact on your organization's security posture. Use this feedback to gradually step up the security; ar the same time, monitor security events for policy violations that may tell you policies are too strict, or might be an indication of suspicious activity warranting further investigation.
DON'T: Underestimate the importance of communication. Executive approval doesn't eliminate resistance. Engage application owners early in the process, so they know how the Zero Trust initiative benefits the company and their project, how they will be impacted by any changes you propose, what the new operational model will be, and what support you need from them.
Executive approval doesn't eliminate resistance. Engage application owners early in the process, so they know how the Zero Trust initiative benefits the company and their project, how they will be impacted by any changes you propose, what the new operational model will be, and what support you need from them.
The Zero Trust team's "quick win" reference projects mentioned above need to be highlighted and celebrated, to help application owners become comfortable with the model, and to retain the full support of top executive management. And make sure your continuous improvement efforts can be measured and communicated, so the results of your Zero Trust effort are understood and appreciated.
These are just some of the best practices we've learned through our engagements with customers over the years that can help you smooth the adoption of Zero Trust. If you have questions, would like to learn more, or just want to share your story, reach out! We'd love to hear from you!