Businesses, Large and Small, Need Zero Trust
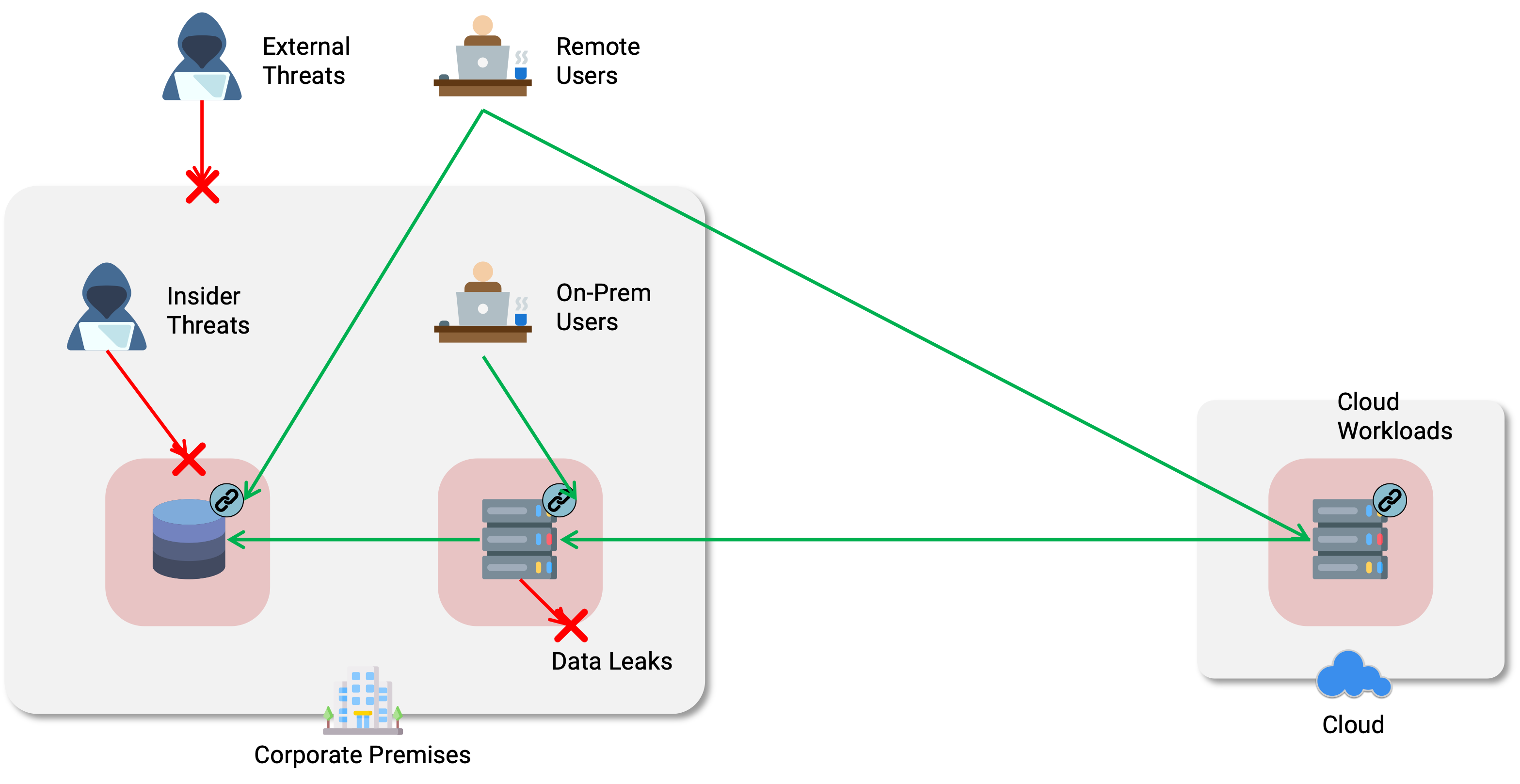
Business have become dependent on digital applications and data to manage the business operations – and the opportunity for hackers to attack them has never been higher. Legacy networks and network security leave those applications open to attack by hackers who can gain access to shared networks, leaving businesses exposed to threats coming from inside or outside the network.
Recognizing the danger, the US Government has directed federal agencies to protect themselves by adopting Zero Trust Security by 2024. But, cyber criminals don't discriminate in their targets. A Zero Trust transformation isn't just for major enterprises; all businesses need a security makeover.