Zentera’s CoIP® (Cloud over IP®) Platform supports enterprises in building a cybersecurity mesh across remote infrastructure environments - enabling Zero Trust connectivity without stitching together distributed network edges for traditional network-level security.
CoIP Platform authenticates applications, workloads, users, and services that are deployed across distributed network silos, and securely connects them using a Zero Trust overlay. With security functions inserted along the path, such as L4-7 firewalls, micro-segmentation and cloaking provided by Virtual Chambers and powerful application identity-based access provided by ZTNA, enterprises can lock down cloud and on-premises servers with consistent policy controls everywhere.
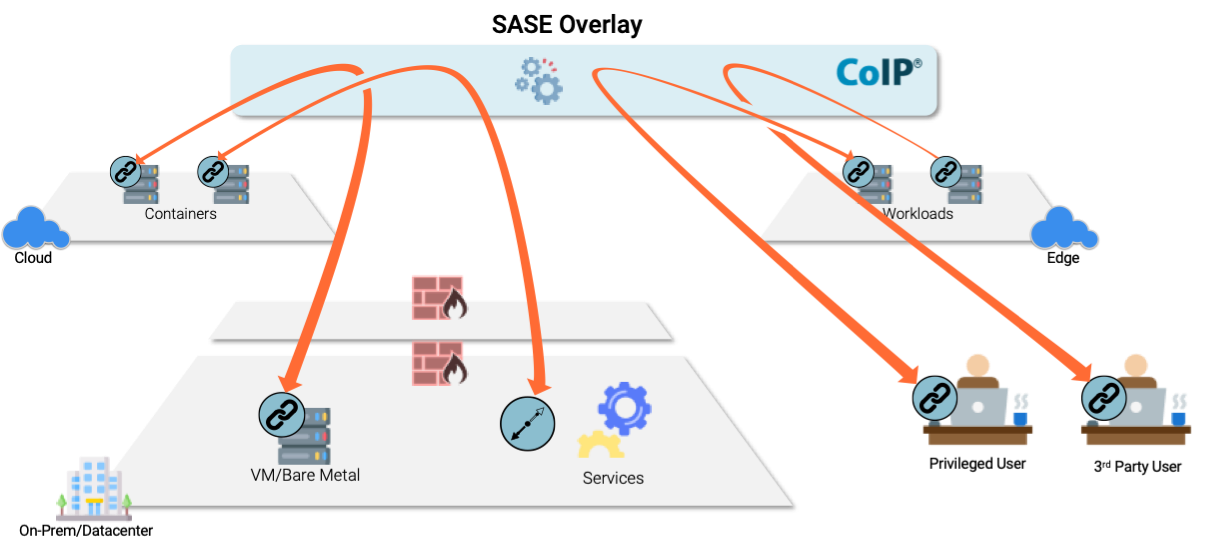
CoIP Platform enables customers to upgrade application connectivity to Zero Trust. CoIP Platform replaces conventional trust based on IP address and blacklisted ports and protocol with server and application identity-based authentication and whitelist policy controls that comprehend the behavior or network accesses.

Satisfy the cloud service provider shared responsibility requirement by deploying a Zero Trust application network in the cloud. You own and maintain the encryption keys. Secure tunnels start and end inside the guest OS, protecting data in transit against snooping, even at the hypervisor level.

Upgrading firewalls and routers for Zero Trust can require heavy lifting, and may require standardizing on a specific vendor. CoIP Zero Trust Security is a completely software-based overlay, and will work in any legacy infrastructure with any combination of vendors.
With CoIP Zero Trust overlay technology, enterprises are able to instantly deploy Zero Trust Security to protect distributed users and applications, regardless of where they are.

CoIP Platform authenticates users, endpoints, and applications, using corporate identity providers, certificates, and other device/app fingerprints.
When a user or application requests access, CoIP Platform checks policy, sets up a CoIP AppLink tunnel for authorized connections if required, and inserts required security functions inline, such as firewall and threat detection/prevention.
CoIP Platform supports nearly any cloud environment, bare metal, or IoT device with agent-based, agentless, and gatekeeper deployment options, and deploys in existing environments without requiring network and security infrastructure changes.
CoIP Platform provides administrators with complete visibility into user, endpoint, and application end-to-end behavior. It provides a rich source of data and intelligence for XDR analytics, as well as control over the cyber kill chain for response and remediation.

“With CoIP, we are able to onboard our design partners and EDA vendors in a matter of days instead of weeks or months, which provides us with a great advantage in our product design and development agility. That is critical in our fast-moving industry.”
“With the CoIP solution, you are literally connecting the one person that needs access to the one resource they need access to and nothing else.”
“CoIP Access Platform’s best-in-class micro-segmentation keeps our customers secure, and we and our customers have saved a significant amount of time in configuration and deployment.”
“With the CoIP Access Platform, we are able to protect our IP and segment our resources across worldwide infrastructures almost instantly.”
Sign up for our newsletter and to be notified of product, solution, and company news.
© 2026 Zentera Systems, Inc. Terms of Service Privacy Policy Open Source