WHITE PAPER
Beyond the Firewall
Legacy network security methods are running out of gas in today's complex and distributed environments. This white paper explains what comes next and how it helps with operational agility.
Get the White PaperOne compromised endpoint shouldn’t mean your entire network is exposed. Zentera wraps critical assets in Virtual Chambers that stop attacks instantly.
Deploy in minutes. Prove risk reduction in days. Scale when you’re ready.
All without redesigning your network.
✓ Fast. ✓ Simple. ✓ Rollback-safe.








A Virtual Chamber is a software-defined security boundary that wraps around any application or asset to ensure only authorized traffic can reach it.
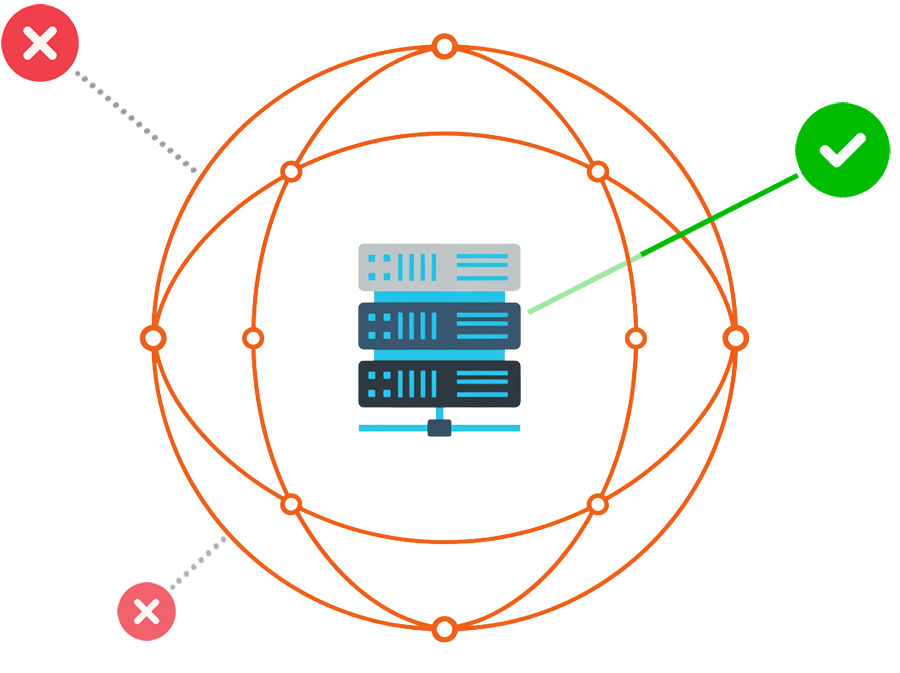
Pick the outcome you need now.
Prove it fast.
The SEC requires disclosure of material cybersecurity incidents. Sensitive R&D IP being accessible from a compromised endpoint on your network can result in board-level exposure.
Create secure zones for sensitive work that minimize data leaks while accelerating productivity.
60% of breaches involve a third party. Every vendor VPN connection is a trust boundary you don’t control.
Give vendors access to exactly what they need. Nothing more.
Nation-state attacks on critical infrastructure hit record levels in 2025. If your network is flat, one compromised device can put your entire operation at risk.
Protect PLCs, SCADA, and legacy systems to ensure operational resilience.
Modern ransomware reaches crown-jewel assets within hours of initial compromise. Perimeter controls don’t help once an attacker is already inside.
Contain lateral access to crown jewel assets, even when the network has been compromised.
Day 1: Deploy and Observe. Week 1: Enforce. Day 30: Expand.
Before Zentera: Flat networks with no segmentation between IT and OT. Lateral movement paths you can’t see. Audit findings you can’t remediate fast enough.
Pick your highest-risk asset — the database, PLC, or application that keeps your CISO up at night. Map its dependencies. That’s your first Virtual Chamber.
Deploy lightweight agents on workloads you control, or agentless inline appliances for legacy and OT systems. No IP changes. No network redesign. No downtime.
Define who and what can reach this asset. Everything else is denied by default. Your blast radius just shrank from “the whole network” to “this one chamber.”
Protects assets with powerful Zero Trust controls.
Works even when access "looks legitimate."
Quantifiable security posture improvements.
Explore our Attack Simulator below to see how protecting selected assets limits damage and maintains operational resilience in the face of cyber attacks.
Every week without taking action is a week where your blast radius is your entire network.
Zentera helps you avoid costly breach remediation and downtime. It also prevents the impact of breaches before your SOC even knows the threat is there.
The question isn't whether you need Zero Trust. It's what another quarter of delay costs your organization.
Enterprise security, without the enterprise overhead.
Works on your existing infrastructure. No IP changes required.
Deploy non-disruptively. Learn policies based on observed application behavior.
Identity and app-centric rules that you can understand and maintain.
Instant undo if anything unexpected happens.
Observe first, enforce later. Prove value before scaling.
“CoIP gives you the security that you need, and at the same time, overlay networking gives you a level of agility that you just don’t have today in a traditional infrastructure.”
“Zentera stands out from other platforms due to their focused ability to allow enterprises to control workloads and avoid the risk of disrupting existing corporate infrastructure.”
“With the CoIP Platform, we are able to protect our IP and segment our resources across worldwide infrastructures almost instantly.”

Legacy network security methods are running out of gas in today's complex and distributed environments. This white paper explains what comes next and how it helps with operational agility.
Get the White PaperMost teams can show measurable risk reduction in days, without impacting running applications.
© 2026 Zentera Systems, Inc. Terms of Service Privacy Policy Open Source