How Zentera Protects Critical Healthcare Systems
Epic, Meditech, and Oracle Health environments are often the most controlled part of a hospital. But ransomware doesn’t need the EHR to shut down care. If clinical devices, building systems, shared services, or lab feeders are disrupted, downtime becomes a patient safety event. Zentera extends Zero Trust enforcement to these exposed systems - fast, agentless where needed, and without redesigning your network.
Key Outcomes
- Reduce downtime risk from ransomware and malware by enforcing least‑privilege connectivity
- Strengthen resilience during surge events and emergencies
- Improve auditability with less workflow friction across care delivery
- Replace implicit zone trust with identity‑based, least‑privilege connectivity between systems
- Stop lateral movement by enforcing what’s allowed and blocking everything else
- Overlay enforcement that complements your existing NAC, firewalls, and visibility tools
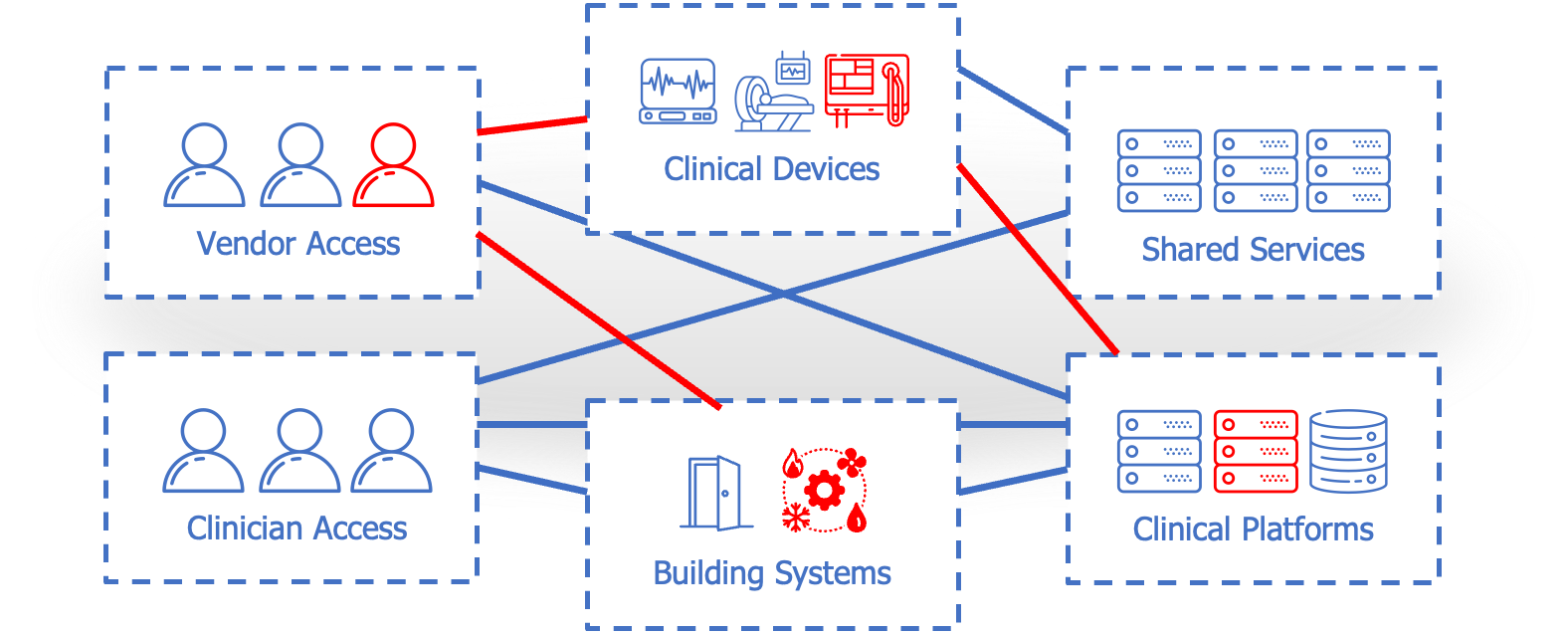
Verified access to only the applications and systems required for care delivery.
Granular, controlled connectivity without broad VPN reach.
An overlay that helps you see what’s talking and enforce what’s allowed—without redesign.
Clinical devices, building systems, shared services, lab/pharmacy workflows, and research environments.
How It Works
Identify the non‑EHR systems most likely to cause care disruption if compromised—and prioritize fast containment.
Inventory and map dependencies for exposed domains: clinical devices, building systems, shared services, lab/pharmacy/imaging workflows, and vendor pathways.
Choose the first scope (one facility, one campus, or one “critical dependency cluster”).
Add enforcement without disrupting care; no multi‑quarter segmentation project required.
Deploy Zentera as an overlay and place enforcement where it fits: inline/agentless for fixed‑function assets and lightweight agents where supportable (e.g., on servers/workstations that broker access).
Connect to identity sources (IdP/Directory) and your logging pipeline.
Replace broad “zone access” with who/what is allowed to reach each critical dependency.
Create least‑privilege policies for the initial scope: clinician access, vendor access, service‑to‑service, and admin paths.
Start with a clear allow‑list for the workflows that must function (lab → interfaces, pharmacy → dispensing, facilities → monitoring, etc.).
Contain disruptions before they spread. Turn a hospital‑wide outage risk into a manageable, isolated event.
Enforce identity‑based connectivity and segmentation to block lateral movement between domains (devices ↔ shared services ↔ clinical platforms).
Reduce reliance on VLAN/firewall exception sprawl by enforcing policy at the overlay layer for the protected scope.
Prove value quickly (days, not quarters), then expand to the next priority system or site.
Validate workflows with clinical ops and IT, tune policies, and expand scope incrementally: one dependency set, building, clinic, or acquired site at a time.
Export enforcement signals to SIEM/SOAR and operationalize alerts for unauthorized access attempts.
At a Glance
Hospital and health system security teams, clinical engineering, facilities teams, and IT leaders focused on clinical continuity
Hospitals, outpatient and dental networks, research/lab environments, distributed clinics, and acquired sites with inconsistent controls
Clinical devices and specialized systems, facilities/building systems (HVAC, power, access control), shared services, lab/pathology/pharmacy workflows, imaging/PACS-adjacent systems, and research networks
Agentless protection where endpoints can’t run security software, identity‑centric least‑privilege connectivity, lateral‑movement prevention, microsegmentation without rule explosion
Deploy in days, not quarters. Start with highest‑risk dependencies and expand as you prove value
Identity providers / directory services, SIEM/SOAR, asset discovery and visibility platforms, existing NAC and firewall programs
The Challenge
Healthcare security programs often focus where funding, governance, and vendor pressure are strongest. That work matters. But patient care depends on systems that are harder to secure: fixed‑function clinical assets, building controls, shared services, and domain‑bridging workflows like lab, pathology, imaging, and pharmacy.
When these are compromised, the outcome isn’t just data loss. It’s downtime: canceled procedures, diverted ambulances, delayed care, and patient safety risk. Cybersecurity is patient safety. Downtime is clinical risk.
What's still exposed:
- Fixed‑function clinical assets that can’t run agents or be patched
- Facilities and building systems converging with clinical operations (HVAC, power, access control, signage, elevators)
- Clinical support systems that bridge domains (lab, pathology, pharmacy interfaces, specialty systems)
What's at stake: operational downtime, data exfiltration/extortion, regulatory exposure, recovery cost, reputational damage, and loss of patient trust.
Why Traditional Approaches Fall Short
Years of exceptions and rule sprawl make zones porous and hard to maintain, especially as environments evolve.
Minor breaches become lateral movement pathways across clinical, facilities, and shared services.
Many medical devices and specialized systems can’t run agents and can’t be patched on typical IT timelines.
The most operationally critical assets remain exposed.
Visibility doesn’t equal enforcement, and NAC coverage can be uneven across converged environments and acquisitions.
You can see risky pathways, but still struggle to close them without disruption.
Traditional ZTNA is a user‑to‑app remote access tool and doesn’t reliably enforce least‑privilege connectivity inside the clinical ecosystem (on-prem users, systems talking to systems, and complex dependencies).
Lateral movement remains possible through trusted internal paths.
The Zentera Approach
Zentera focuses on enforcement: stopping lateral movement and tightening access to critical dependencies, especially where agents and redesigns aren’t feasible.
Overlay Enforcement Across Domains
Agentless Where Needed, Lightweight Agents Where Possible
Microsegmentation Without Rule Explosion
Reference Architecture
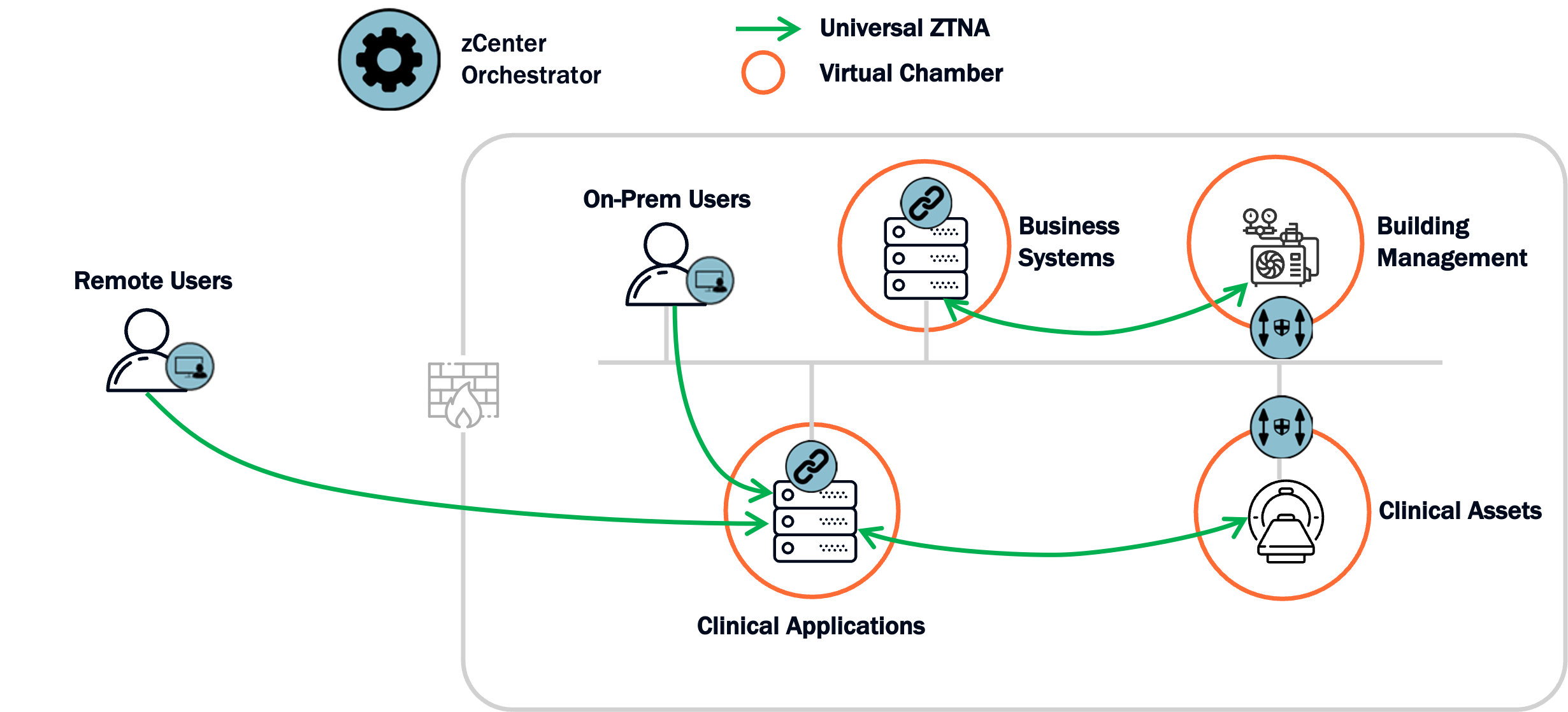
This architecture shows how Zentera overlays the healthcare environment and enforces least‑privilege connectivity between clinicians, vendors, clinical platforms, shared services, clinical devices, and building systems—reducing lateral movement and containing blast radius
Identity-based Access
Verified clinician and vendor access decisions replace implicit trust.
Overlay-based Enforcement
Zentera enforces allowed connectivity for the protected scope, without network redesign.
Critical Dependencies Protected
Shared services, facilities systems, and clinical support workflows are tightened so disruptions don’t cascade.
Clinical Platforms Remain Stable
Keep existing EHR governance; extend protection to what attackers use to stop care.
What Changes
- From “zone trust” to identity‑based, least‑privilege connectivity
- Lateral movement paths are reduced and controllable
- You can start with the highest‑risk dependencies and expand incrementally
What Stays the Same
- Core network architecture and existing security stack (NAC, firewalls, visibility)
- Clinical workflows (validated and tuned during rollout)
- EHR governance model: this extends it to the rest of the clinical ecosystem
Key Capabilities
Simplify segmentation programs that have stalled under VLAN sprawl and exception overload—without adding complexity to an already stretched team.
Start protecting highest-risk dependencies in days, not quarters—without rip-and-replace projects that compete with clinical priorities.
Extend the value of your current NAC, firewalls, and visibility tools by adding the enforcement layer they lack—not replacing what you've already built.
Protect medical devices, building systems, and specialized clinical assets that can't run agents or be patched on typical IT timelines.
Enforce identity-based policies that control who and what can reach each system—clinicians, vendors, shared services, and clinical support workflows.
Shrink reachable paths between clinical devices, facilities systems, shared services, and platforms so a breach in one domain can't cascade into others.
Implementation Details
Deployment & Operations
Outcomes & KPIs
Security
Operational
Business
Proven Results
Agility you just don't have in a traditional infrastructure
The ability to grant vendors access to specific applications without VPN has transformed how we manage third-party maintenance.
Related Resources
Protecting Critical Healthcare Systems
Learn how Zero Trust protects clinical devices, building systems, and shared services to reduce downtime and patient safety risk.
DownloadSecuring Healthcare IT & OT
On-demand webinar with industry experts - insights on microsegmentation, HIPAA compliance & ROI.
WatchWhat Is Zero Trust Security
Learn how Zero Trust redefines cybersecurity through continuous verification, minimizing risk, and enhancing data protection for organizations.
ReadReady to Protect Your Healthcare Operations?
Talk to our architects about your specific security challenges.
Talk to an Architect
Get expert guidance on your OT security strategy
Schedule a Call 30-minute consultation