How Zentera Protects Critical Intellectual Property
Critical IP has to be accessible to create value—source code, chip designs, models, and R&D data must move between internal teams and trusted partners. That same access is what makes IP easy to leak.
Zentera shifts IP protection from “detect at the edge” to “enforce at the workload.” Virtual Chambers cloak crown‑jewel systems so they’re unreachable by default, then allow access only through approved identities and approved methods.
Legitimate work continues, but leak paths collapse.
Key Outcomes
- Prevent IP theft by making crown-jewel systems unreachable by default - even from users already "inside" the network.
- Accelerate secure collaboration with partners and contractors: spin up a project chamber fast, and tear it down cleanly when work ends.
- Reduce blast radius from insiders and ransomware without slowing engineering workflows or partner onboarding.
- Enforce least-privilege access with deny-by-default reachability, workload cloaking, and identity-based policy for employees, contractors, and partners.
- Block common leak paths (copy/paste, in-session file transfer, USB redirection, SSH tunneling/SCP) and require approved, logged transfer channels.
- Export audit signals to your SIEM/logging stack. See who accessed what, how, and what was blocked.
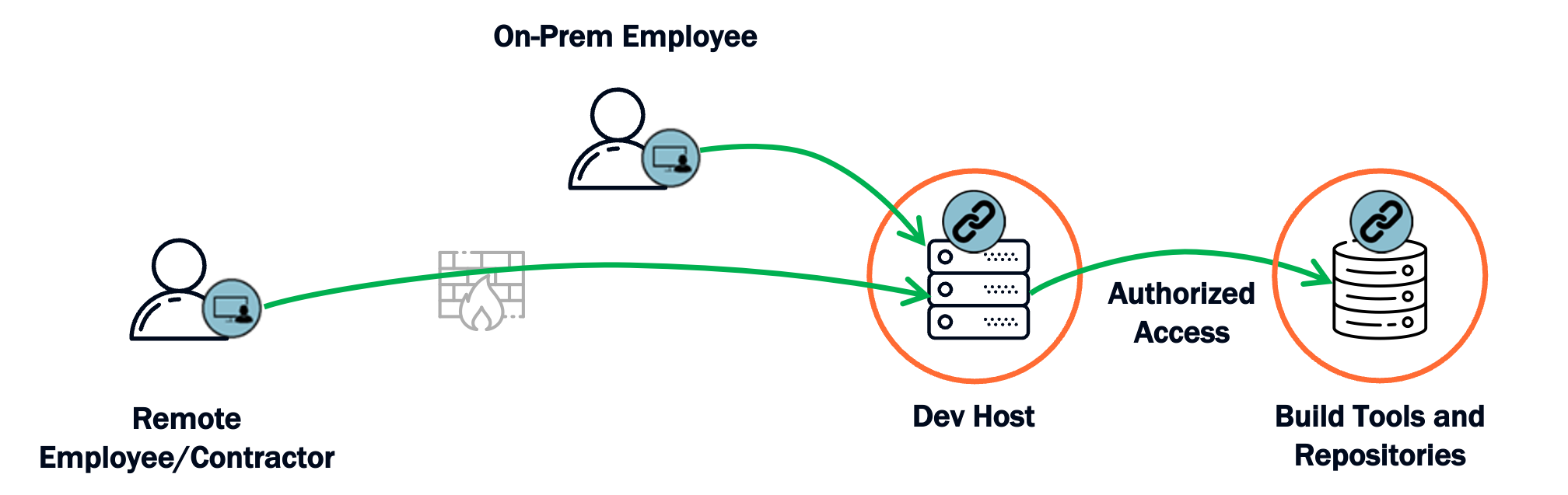
Remote contractors, vendors, and partners access development servers through ZTNA
Environment where users can interact with IP using secured and approved methods
Employees, admins, and support personnel gain access through Universal ZTNA
Internal access scoped to the user role and project
How It Works
Identify the crown‑jewel IP that would materially impact competitiveness if leaked.
Map where IP is stored/processed (repos, file shares, tools and build servers, etc.) and who needs access.
Document required dependencies (IdP/AD, license servers, CI/CD, artifact repos) so protection doesn’t break workflows.
Add protection without slowing engineering. No network redesign or re‑IP required.
Deploy the Zentera control plane and connect to your IdP to leverage your existing directories/MFA.
Place enforcement where it fits: lightweight agents where supportable and inline/agentless enforcement where needed.
Turn “who should have access” into enforceable policy, down to the approved access method.
Create a Virtual Chamber around IP workloads and set deny‑by‑default rules for inbound/outbound paths.
Define least‑privilege policies for user/partner access (RDP/VNC/SSH/Web/approved clients) and enable anti‑leak controls.
Keep work moving while collapsing leak paths that turn “legitimate access” into IP loss.
Block risky behavior by default (copy/paste, file transfer, USB redirection, SSH tunneling/SCP) unless explicitly allowed.
If file movement is required, route it through an approved, logged transfer channel with optional scanning.
Prove value quickly, then expand by program, partner, or geography.
Validate workflows with R&D and Security, tune policy, and operationalize alerts for blocked/unauthorized attempts.
Scale using repeatable templates for new projects, vendors, and acquired teams—without firewall ticket churn.
At a Glance
Security leaders, R&D/engineering leadership, IP protection program owners, and IT/security architects
High‑tech and semiconductor, aerospace/defense, pharma/biotech, and any organization that must share sensitive IP across teams and partners
Source code, chip designs/PDKs, build pipelines, AI/ML models and training data, proprietary research datasets, sensitive documentation and design artifacts
Virtual Chambers (in‑place microsegmentation + cloaking), secure partner access without VPN sprawl, enforced access methods with anti‑leak controls, application‑aware policy enforcement
Deploy in hours/days—not months. Start with one crown‑jewel scope and expand incrementally.
Identity providers / directory services + MFA, SIEM/SOAR, optional content scanning for approved transfer channels, existing firewall/NAC programs (complementary)
The Challenge
Critical IP is the lifeblood of many enterprises, and because it’s digital, it’s easily copied and quietly exfiltrated. Many organizations rely on edge detection (DLP) and monitoring, but IP theft often looks like legitimate access. By the time you confirm a leak, the asset is already gone.
The real question is not “How do we keep attackers out?” It’s: can we protect crown‑jewel applications and data even when credentials, endpoints, or partner access paths are compromised? That requires enforcement: tight control over reachability and approved methods to access and move IP.
What's at stake: loss of competitive advantage and time‑to‑market, contractual and regulatory exposure, recovery cost, litigation risk, and long‑term reputational damage.
Why Traditional Approaches Fall Short
IP theft often looks like authorized access, and sensitive content can be packaged in ways that evade signatures.
You learn about the leak after the asset has already been copied out.
Network-centric isolation is slow and brittle, and exceptions accumulate as projects and dependencies change.
Teams expand trust or bypass controls to keep work moving—creating new leak paths.
VPN joins networks. It’s hard to scope access to specific assets and specific safe methods without complex infrastructure.
One compromised credential or partner device can create broad reach into sensitive environments.
Permissions control access to the file—not what happens after it’s opened (copy, sync, forward, screenshot, export).
Insider leaks and accidental exposure remain likely even with “least privilege” shares.
Response is after-the-fact. Attackers optimize for leverage before containment catches up.
Expensive incident response with irreversible IP loss.
The Zentera Approach
Zentera focuses on enforcement: making critical IP workloads unreachable by default, then allowing access only through approved identities and approved methods, so theft paths disappear without disrupting legitimate work.
Virtual Chambers Contain IP and Stop Data Leaks
Approved Access Methods + Anti-Leak Controls
Application‑Aware Enforcement for Risky Tools and Ransomware
Reference Architecture
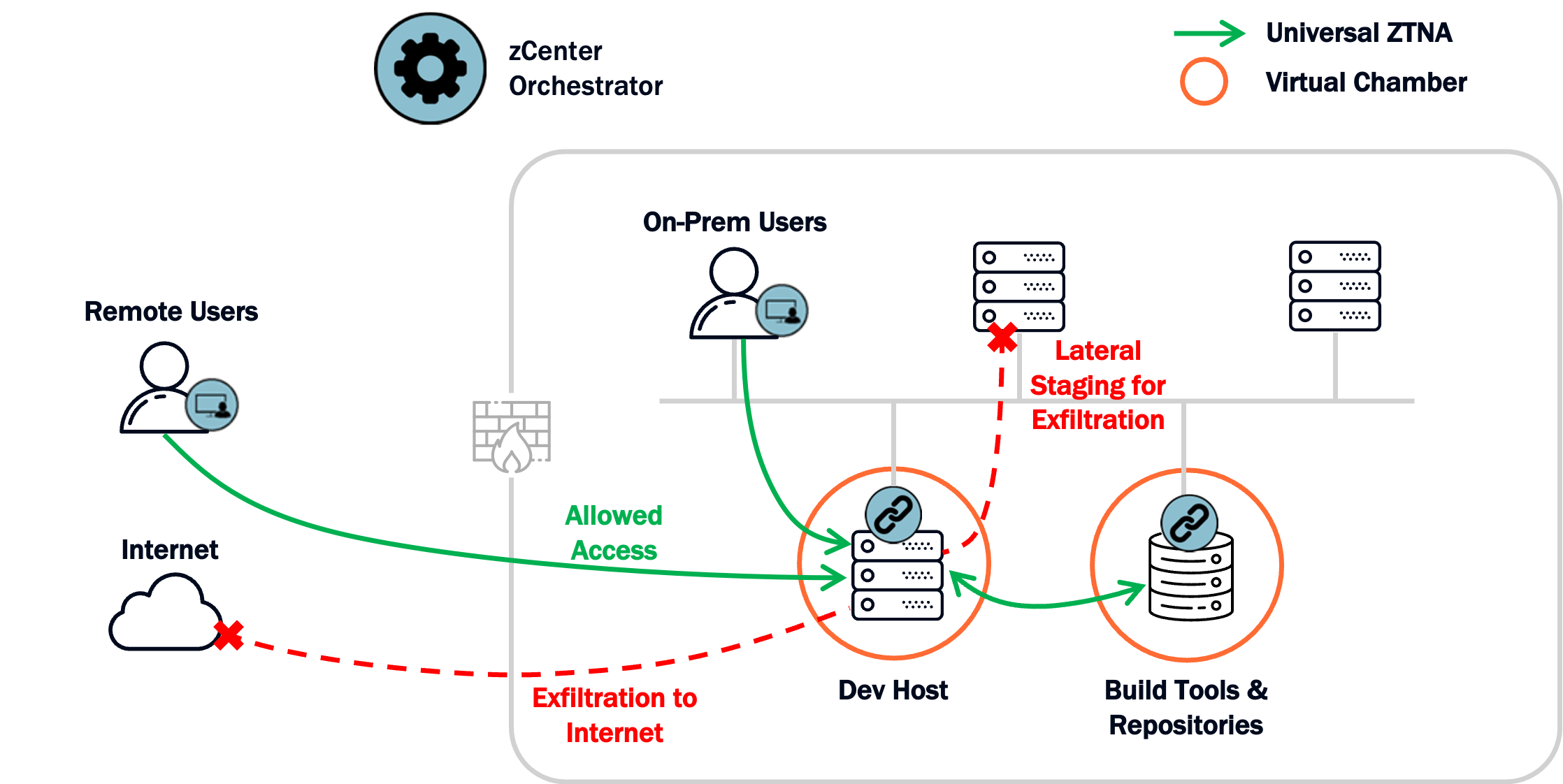
This architecture shows how Zentera overlays your existing environment to create a chambered environment to contain your IP and enforce least‑privilege access for employees, contractors, and partners. Chambers block exfiltration, while approved access methods block exfiltration through the user's machine.
Identity-based Access
Every session is authenticated via your IdP/MFA, then explicitly authorized by policy - no implicit trust based on network location.
Crown‑Jewel IP Cloaked
Chambered IP workloads are unreachable by default and not easily discoverable through scanning or inherited trust paths.
Enforced Safe Access Methods
Access is granted through approved methods (RDP/VNC/SSH/Web/approved clients) with anti‑leak controls that block risky transfer behavior.
Auditable Transfer & Control
Allowed access and blocked attempts are logged; approved transfer channels can be controlled and monitored for governance and compliance.
What Changes
- From “network trust” to identity‑based, least‑privilege access to specific IP workloads
- Crown‑jewel systems become unreachable by default and harder to discover
- Risky transfer methods are blocked by policy; approved channels are governed and auditable
What Stays the Same
- Your core network architecture (no re‑IP, no rip‑and‑replace)
- Existing tools and workflows, validated and tuned during rollout
- Your existing security stack (identity, SIEM, endpoint tools) is complemented, not replaced
Key Capabilities
Onboard contractors and vendors in hours—not weeks—with access scoped to exactly what each project requires.
Close the gap between "authorized access" and "IP walks out the door" by blocking the leak paths that policies alone can't stop.
Go live in days and show auditors exactly who accessed what, how, and what was blocked—without months of implementation.
Instantly microsegment and cloak IP workloads in place so they’re unreachable by default. No network redesign required.
Constrain high‑risk behaviors (tunneling, SCP, USB redirection, copy/paste) and route approved transfers through logged, scannable channels.
Tie policy to identity, device, and application/process context to restrict unauthorized tools and limit the value of stolen credentials.
Implementation Details
Deployment & Operations
Outcomes & KPIs
Security
Operational
Business
Proven Results
Agility you just don't have in a traditional infrastructure
With the CoIP Platform, we are able to protect our IP and segment our resources across worldwide infrastructures almost instantly.
Ready to Protect Your Critical IP?
Talk to our architects about your specific security challenges.
Talk to an Architect
Get expert guidance on your OT security strategy
Schedule a Call 30-minute consultation