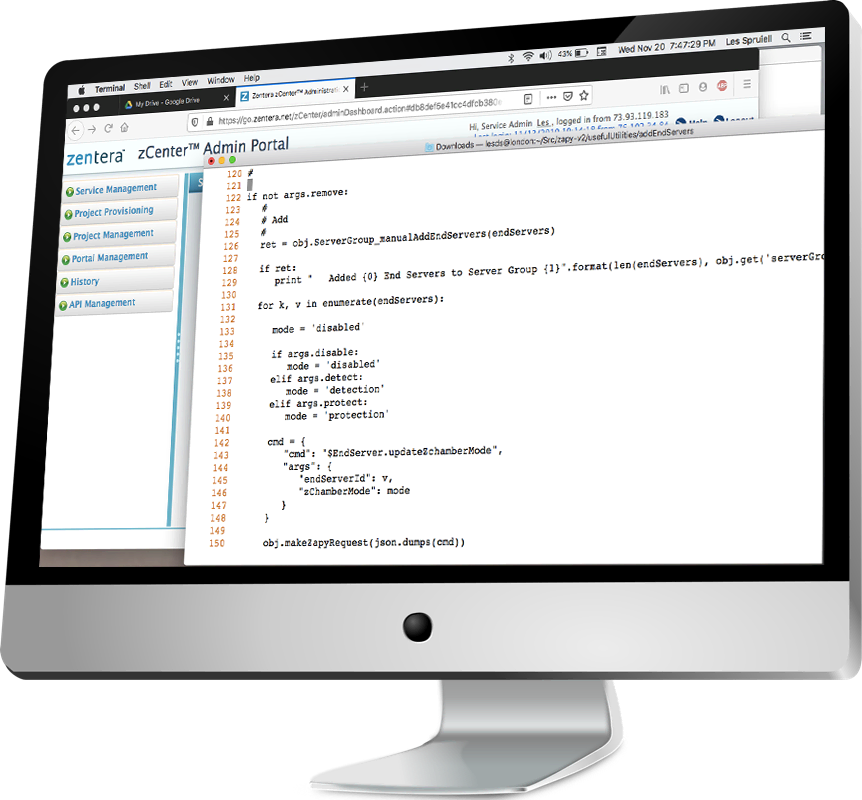
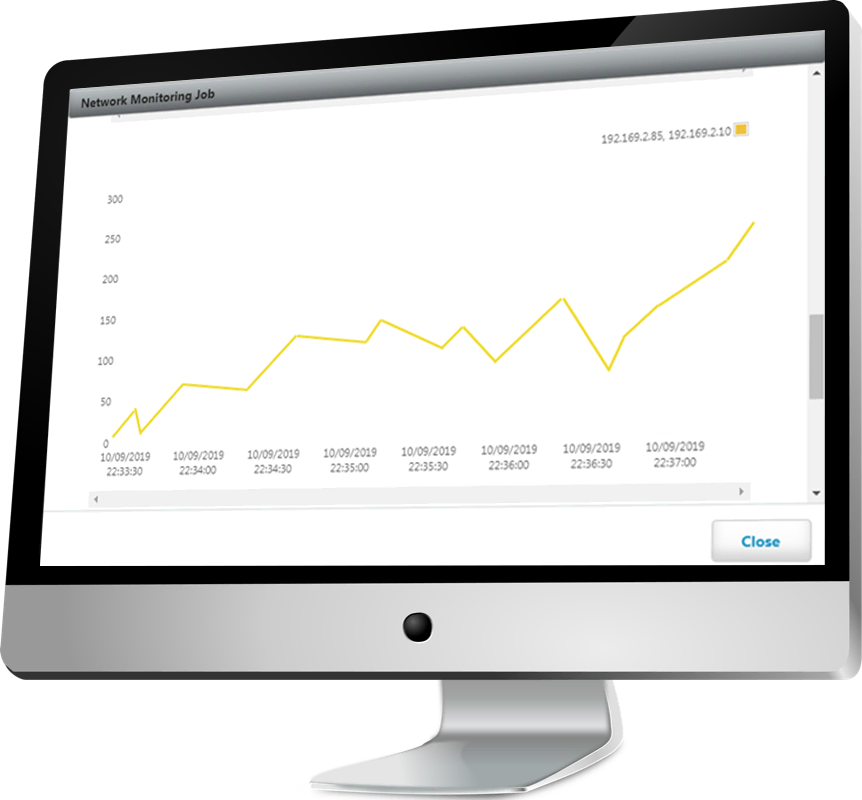
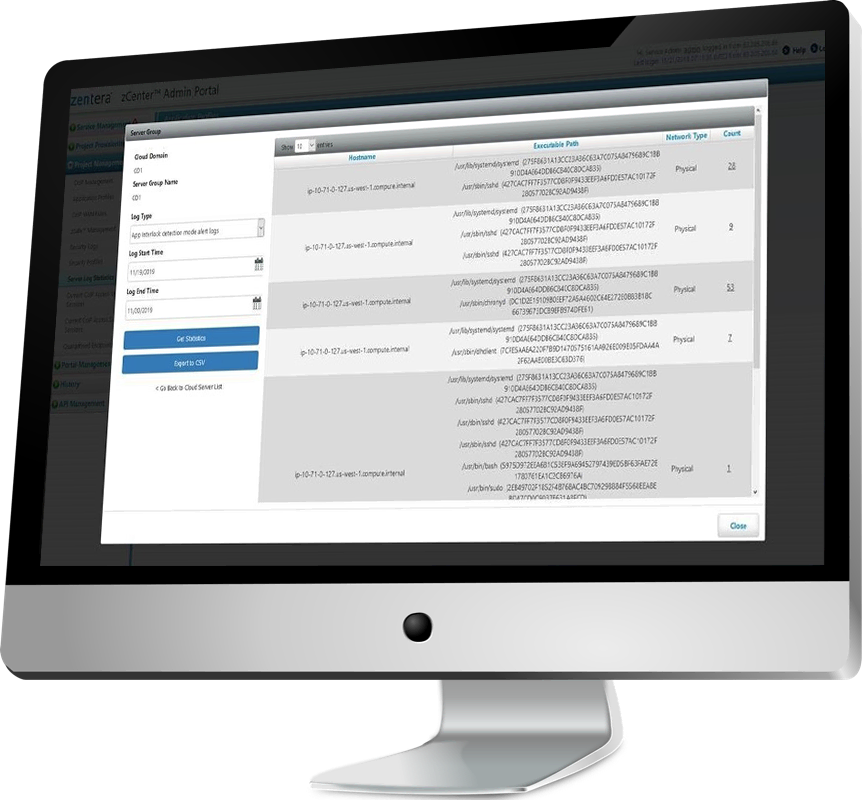
Application communications are defined by whitelist policies, creating security by default. Policies are end-to-end, creating a single, global policy database that defines who can access what resource.
The Application Profile concept enables a set of policies to be defined as a template and used again and again.