The Simple Economics of Zero Trust

Last month, the Federal Reserve raised interest rates for the 8th time in a row, corresponding to the steepest rise in rates since 1988. And last week, BofA researchers cautioned that the Fed may need to raise rates as high as 6% before they're done. The resulting stock market pains and worries about the future have triggered rounds of belt-tightening for companies of all sizes. Projects are being reprioritized, headcount is "rationalized," and teams are being asked to do more with less. Chances are your company's in this boat, too.
But ransomware is recession-proof, and recruiting malicious insiders can't be harder in the current environment. That means that you can't just scale back your efforts to secure your organization from actors with malicious intent.
That sounds like an assignment straight out of Mission: Impossible. How can you maintain or even improve your cyber posture when it's time for tight control over budgets and headcount?
Good news: there's an answer for that, and it won't break the bank. That answer is to deploy Zero Trust, using software-defined network security solutions like CoIP Platform. It's not nearly as difficult or as expensive as you think - but you do need to think differently!

Think small
In our line of work, we instinctively seek out large scale solutions. We want to solve a problem once and for all. "Users getting phished? Let's roll out phishing training and upgrade our endpoint protection for the entire company. Hackers in the network? Let's implement asset discovery and network detection and response. And make sure we get the latest threat feeds!"
The problem with large scale solutions is that they are large scale. The tools are expensive, require headcount to run and specialized training to decipher, and require significant coordination and communication to roll out. And often times, that scale means the protections are so broad that their actual protective value is diffuse.
The truth is that spreading a large expense across a wide range of assets and data can be a waste - not all data is created equal. If you look closely at the data that drives your organization, there will be a very small set that are really critical for operations or could create major headaches if they're breached, and a long tail of data that are not quite so important.
Yes, technically speaking the historical records of the office trash pickup are company documents, and yes, someone might be able to infer something from the volume or frequency of your service, but let's face it. That's just not high value, compared to your ERP system. Wouldn't it make more sense to just deploy meaningful protection for the ERP system?
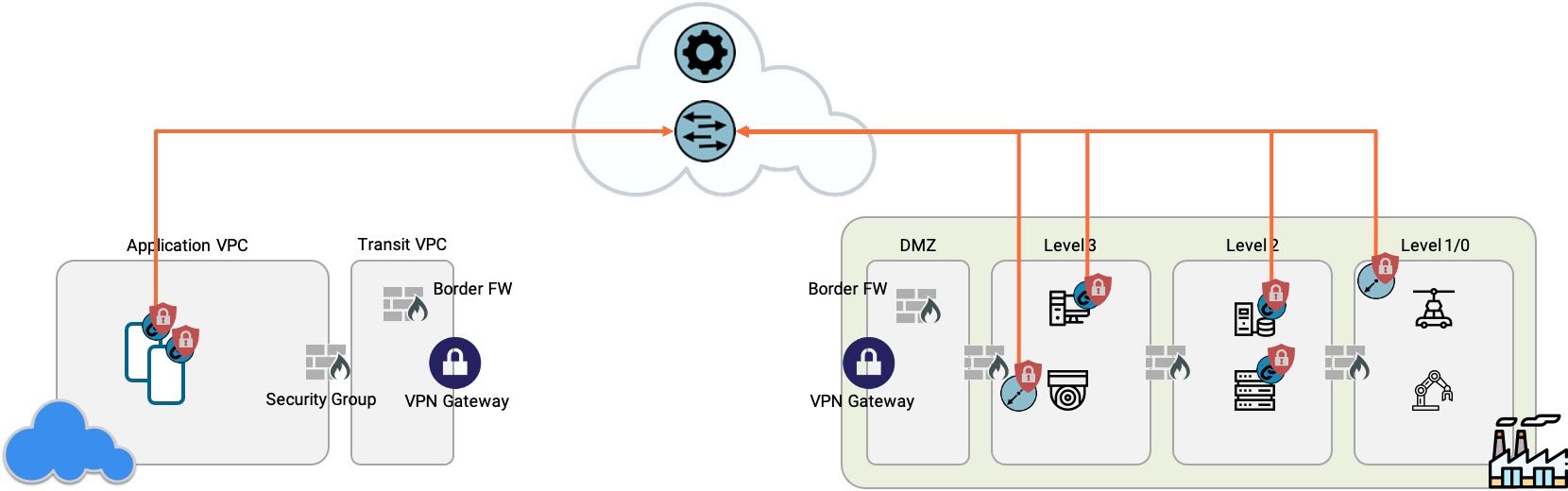
CoIP Platform Zero Trust allows you to do just that - cloak the ERP system from unauthenticated and unauthorized network activity, so even if hackers are in your network, they won't be able to attack the ERP with ransomware or exfiltrate your financial data. Done properly, Zero Trust doesn't affect anything else in your network, letting you dial in an appropriate project scope to balance the risk reduction Zero Trust will provide against the expense of implementation and support.
Discover the latest guidelines in cybersecurity!
Don't sweat the threats
One of the challenges that come naturally with any new cybersecurity tool is making sense of its output. You need to communicate what this tool is doing, both for actionable information (e.g. threat hunting) and for communicating with management.
Zero Trust is a bit different. Zero Trust security's default deny model means that the only traffic that will get through to your applications and data has gone through rigorous authentication and authorization checks. A Zero Trust system will warn you when it detects an unauthorized access so that you could check it out, but you can rest assured that this access was blocked. With your most critical applications under lockdown, you are free to take action and remediate on your own timetable, with the resources that you have. Even if you are breached, you won't make it to the 10 o'clock news.
Think about the alternative
One of the main benefits from Zero Trust comes from the default deny model, typically implemented with software-defined micro-segmentation. If you had to create this using traditional network infrastructure techniques, you could get close - you'd have to set up a VLAN for the application, move the application inside, grant other machines access to the VLAN and filter it with ACLs. It wouldn't be Zero Trust (it would be missing identity), and worse, it would involve pulling a lot of cables and a lot of network reprogramming that would be disruptive to the application. If you have to do this for more than one or two applications, get ready for some downtime.
 Zentera's CoIP Platform combines the segmentation and the access you need in a single, integrated tool. More advanced overlay-based Zero Trust can deploy transparently over existing applications and networks. In many cases, securing an application with Zero Trust can be done in just a few hours. This saves significant time and effort, reducing the number of tickets and change requests you send to IT.
Zentera's CoIP Platform combines the segmentation and the access you need in a single, integrated tool. More advanced overlay-based Zero Trust can deploy transparently over existing applications and networks. In many cases, securing an application with Zero Trust can be done in just a few hours. This saves significant time and effort, reducing the number of tickets and change requests you send to IT.
An ounce of prevention is worth a pound of cure
With all of the cost-saving advantages and benefits of Zero Trust security, hopefully you will make a decision to look into it as a way to deploy strong security controls for your most critical applications and data in a cost-effective way with minimal effort.
On the other hand, doing nothing also saves money - up until you get breached. Trying to remediate a breach is expensive and nerve-wracking even in the best economic environment. In today's environment, though? Nobody has the time or budget. And, let me tell you, the ransomware gangs are counting on that.
Ready to do something about it? We invite you to explore how we can help you apply Zero Trust security to protect your most critical assets and data, and to connect with our solutions architects for a deeper discussion.