Zero Trust Unveiled: 5 Common Myths

Zero Trust is one of the most frequently discussed topics in cybersecurity, but it’s also one of the most misunderstood. It’s not because there’s not enough information out there - on the contrary, there is way too much written about Zero Trust! The excess of content is generated by cybersecurity vendors looking to associate old products with new and trendy topics.
Despite the hype, Zero Trust is not just another passing fad in cybersecurity. Rather, it has the potential to transform security for the organizations that have adopted it. Failing to understand the true nature of Zero Trust networks can leave your organization vulnerable, even if you’ve spent millions on “Zero Trust projects.”
This blog aims to clarify and dispel five of the most common misconceptions we’ve heard when interacting with customers or have seen repeated in media coverage. They are:
- Zero Trust is Exclusively for the Federal Government
- Executive Management Can't Grasp Zero Trust
- Zero Trust is Supposed to Protect My Users
- Upgrading Existing Tools Will Get Me To Zero Trust
- Zero Trust Requires an Expensive Infrastructure Upgrade

Myth #1: Zero Trust Networks is Exclusively for the Federal Government
The Biden Administration certainly put Zero Trust on the map when it issued Executive Order 14028 in 2021, directing NIST and OMB to create standards and guidelines for Zero Trust networks and mandating that all Federal agencies adopt them by the end of 2024.
However, the benefits of Zero Trust aren’t limited to government agencies. The primary objective of Zero Trust is to safeguard applications and data against cyberattacks from malicious actors who are already in your network. That’s a worthy goal for all organizations, regardless of their size or industry.
As I wrote in my recent blog about the National Cybersecurity Strategy, the federal government is creating incentives for commercial entities to adopt Zero Trust - for example, by making adoption of Zero Trust network practices a requirement for government contracts, and by making secure development practices a requirement to avoid product liability claims arising from cyber incidents. While the push to overhaul security definitely started in the government, agencies are signaling their commitment to drive these practices into the rest of industry.
CISOs and CIOs for all types of organizations are well-advised to plot a course for Zero Trust adoption.
Discover the latest guidelines in cybersecurity!
Myth #2: Executive Management Can’t Grasp Zero Trust
It’s common for people to assume that Zero Trust is too complex for executive management to comprehend. The CISA Zero Trust Maturity Model, which defines the theory of Zero Trust, is complex and is written for practitioners seeking guidance on how to design and implement a Zero Trust network solution.
But executive management are responsible for aligning business priorities and allocating resources, ultimately bearing the responsibility for business risk. You can bet top management understands that protecting key assets even when hackers are in the network makes sense - which is what Zero Trust is all about.
It’s the CISO’s responsibility to translate Zero Trust networks into a business initiative for risk management. Instead of pitching a “Zero Trust transformation” to the CEO, CFO, and board, consider framing your Zero Trust initiative as a risk mitigation strategy. Examples of business risk reduction initiatives that can be supported with a Zero Trust Architecture include:
- Shielding intellectual property against insider threats and exfiltration
- Protecting critical operational assets (e.g. databases and devices) against ransomware
- Establishing least-privilege hybrid access between cloud instances and on-prem resources and data
- Cloaking sensitive business initiatives, such as artificial intelligence (AI)
Executives are aware that Zero Trust exists, and are absolutely interested in solutions that can reduce cybersecurity risk. Organizations that misuse the Zero Trust momentum with conservative and incremental changes may miss the opportunity to make significant reductions in overall business risk.
Myth #3: Zero Trust Networks is Supposed to Protect My Users
This is an extremely common misconception, especially because many “Zero Trust” solutions share many of the same feature keywords, such as identity. If it identifies users and enforces some security, it’s Zero Trust – right? Wrong.
For example, people commonly think of a secure web gateway (SWG) as a Zero Trust network solution, but an SWG serves a different purpose.
An SWG protects users from threats on the Internet as they browse the web or access SaaS applications. It scans for threats such as shady Internet destinations, phishing attacks, and drive-by download attacks.
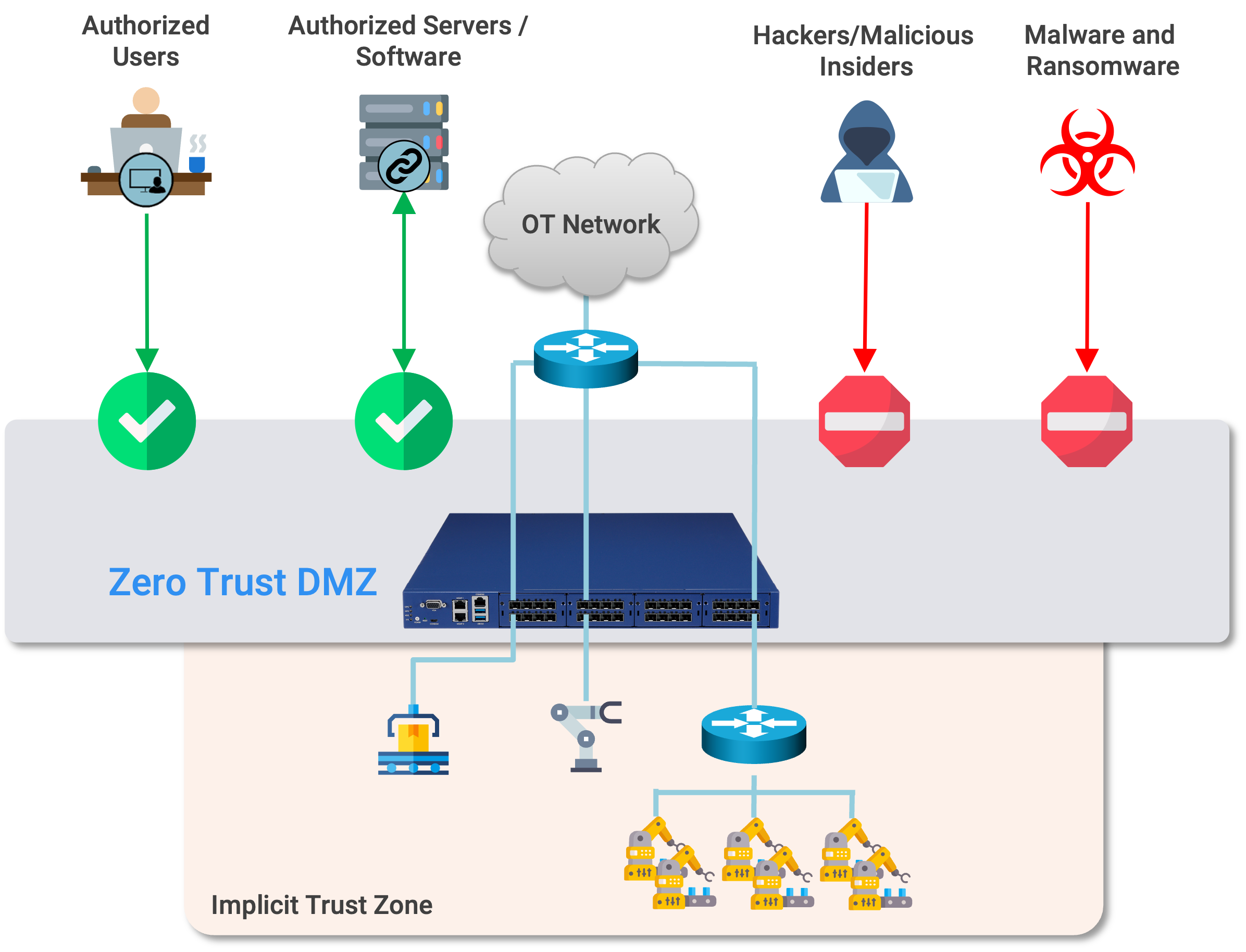
Is that Zero Trust? Let’s reference the definitive Zero Trust Architecture spec, NIST SP800-207.

We can see that a Zero Trust Architecture is deployed to protect high-value assets, such as applications, databases, or devices. The user device is always in the untrusted zone, and undergoes explicit trust checking to validate before it can access the asset in the implicit trust zone. In this case, the user device is not protected from threats - it is the threat.
I am not saying that SWGs don’t make sense (they do) or that you should not use them (you should), but it’s pretty clear that a SWG is not a NIST SP800-207 Zero Trust Architecture. The threat model is completely different. Zero Trust is not about the user device.
Myth #4: Upgrading Existing tools Will Get Me to Zero Trust
When it comes to Zero Trust adoption, cybersecurity vendors often tell customers to “start with what you have.” These vendors are usually trying to convince you to invest more in their particular tool, reasoning that you can at least claim you are moving toward Zero Trust maturity.
“Start with what you have” sounds like a very logical thing to do. Shouldn’t you want to leverage your existing tools?
And that is precisely what makes this argument particularly dangerous. Most of the time, that thinking will not lead you to actual Zero Trust.
Let’s analyze this line of reasoning.
Firstly, increasing investment in new tools without aligning them to specific business risk reduction initiatives can be a waste of time and money, distracting from actual risk reduction. For instance, doubling your spend on identity and access management may improve the Identity pillar of the CISA Zero Trust Maturity Model, but may provide only incremental benefits that don’t really impact the real risks your organization faces.
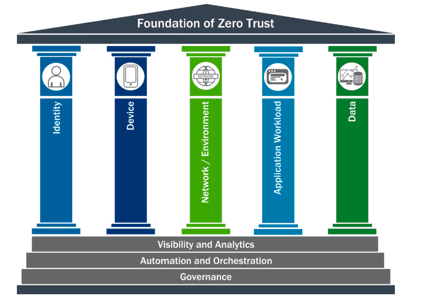
Second, investing in one set of tools without considering how they will interoperate with other tools may not achieve Zero Trust. The CISA Zero Trust Maturity Model defines five pillars, but also defines a critically important foundations of Visibility and Analytics, Automation and Orchestration, and Governance that span all five. Focusing on a pillar as a stovepipe - for example, without ensuring that your identity solution and your network segmentation solution can talk to each other - can leave you unable to enforce an actual Zero Trust policy. In the worst case, you may end up with stranded investments in tools that need to be decommissioned in favor of true Zero Trust.
Before taking steps toward Zero Trust, identify the business goal first. This way, you can determine how well your proposed solution aligns with that goal before you start investing. This approach is outlined in OMB’s M-22-09, which guides agencies to first implement Zero Trust well for one application first before scaling it across the organization.
Myth #5: Zero Trust Requires an Expensive Infrastructure Upgrade
This is one of the biggest concerns we hear from enterprises who are looking at Zero Trust. Customers already know that network techniques like VLANs and VRFs are too operationally complex to implement Zero Trust’s requirement for application segmentation, and that something new needs to be done.
As we saw above, Zero Trust is about applying protection to a specific application or asset to reduce business risk. So it is not necessary to take an “all-or-nothing” approach to Zero Trust – you can achieve some risk reduction and benefit, even if you use decide to change some parts of your infrastructure.
But enterprises - especially mid-size and large enterprises - have complex global networks, evolved over years of expansion and acquisition. Data centers, branch offices, colocation, and now clouds are all connected with a range of routing, switching, and firewall vendors, each with its own technology stack.
Scaling Zero Trust to the global organization may require standardizing the worldwide infrastructure on a single vendor technology stack. Even if possible, this is undesirable.
The good news is that you don’t need to touch network infrastructure at all in order to segment applications for Zero Trust. A number of cybersecurity vendors have developed micro-segmentation solutions, which are powerful, software-defined ways to implement the necessary segmentation.
Some vendor solutions take control of your infrastructure to do this - managing routing tables, access control lists and firewall rules. This can create risks to your network from bugs in the tool, and can also amplify the speed and reach of configuration errors, which can propagate quickly and affect other users and applications.
At Zentera, we use a combination of agent-based and agentless models to implement application segmentation without touching your network settings. Our zLink software agents deploy to the OS of machines that need segmentation, while high-value devices and machines that cannot accept an agent can be protected with our inline Zero Trust Gatekeeper.
These approaches reduce the scope of changes and minimize the risk that software-defined segmentation could affect other applications and users on the network. They also enable organizations to deploy a Zero Trust Architecture as an overlay, on top of any network or compute infrastructure, simplifying the implementation of Zero Trust security for brownfield applications and assets.
Implementing Zero Trust does not need to be a daunting or expensive task. The five myths we have debunked show that there are effective and meaningful ways to use Zero Trust to manage business risk. By focusing on specific business goals, leveraging software-defined overlay solutions, and choosing the right vendors, organizations of all sizes can achieve the benefits of Zero Trust, including lower cyber risk, increased data protection, and enhanced compliance.