How Zentera is Used
Ransomware succeeds when compromised identities and endpoints can reach what matters most. Zentera adds a Zero Trust enforcement layer in front of critical applications and data. Attackers may land, but they can’t spread, explore, exfiltrate, or encrypt at scale.
Key Outcomes
- Containment by design: ransomware incidents stay scoped instead of becoming outages
- Critical services stay available: enforce access boundaries around “crown jewels” without redesigning networks
- Faster response, clearer evidence: unauthorized access attempts stand out and can be exported to your SIEM/SOC
- Protected applications are unreachable by default and exposed only through explicit policy
- Every connection is verified and authorized (user‑to‑app and app‑to‑app)
- Virtual Chambers restrict east‑west traffic so one compromised host can’t become many
Users, devices, and applications requesting access
Protected applications, servers, and data
Lightweight agents enforce access at the workload
Central policy engine and identity verification
How It Works
Add a Zero Trust enforcement layer in front of critical apps without redesigning the network - so you can reduce ransomware impact fast.
Stand up the Zentera control plane and onboard the first protected application (start small: 1 app).
Place enforcement where it fits your environment: lightweight endpoint proxy where supportable + inline/agentless enforcement where required; integrate with your IdP and logging pipeline.
Decide what “must not go down” first (your crown jewels) and restrict access to only the people and systems that truly need it.
Select 1–3 high-value targets (e.g., file shares, identity services, ERP/finance, sensitive databases) and define the protection boundary per application.
Create initial least-privilege policies: who/what can access each protected app (users, admin roles, vendors, service-to-service), and set a default-deny posture for everything else.
Validate real access needs before locking things down, so protection improves without breaking workflows.
Use learned/suggested policies as a starting point, then review with app owners and security to finalize the allow-list (including exceptions and change workflow).
Make critical apps unreachable by default so ransomware can’t spread, discover targets, or encrypt/exfiltrate at scale.
Use application-centric isolation (Virtual Chambers) to restrict east‑west movement into protected apps and contain blast radius if an endpoint or credential is compromised.
Treat blocked access attempts as high-signal early indicators of breach, and use reporting to support leadership, insurance, and audit conversations.
Export allow/deny events to SIEM/SOAR and alert on policy violations targeting protected apps (credential misuse, lateral movement attempts).
Operationalize: tune policies as apps change, expand protection app-by-app, and periodically review access posture for “crown jewels.”
At a Glance
Security teams and IT leaders who need ransomware containment across hybrid environments without slow segmentation projects
Hybrid IT (on‑prem + cloud), multi‑site enterprises, M&A integration, third‑party/vendor access, regulated environments
Business‑critical applications and data (ERP/finance, file stores, databases, identity services, source code repositories, operational applications)
Application cloaking, least‑privilege access, rapid application microsegmentation, secure vendor/admin access without broad network trust
Universal ZTNA, Virtual Chambers, Overlay Network, zLink connectors
First critical application protected in days. Risk reduction compounds as more “crown jewels” are added.
Identity providers (SAML 2.0, OAuth/OIDC, LDAP), SIEM/SOAR platforms, asset discovery tools
Get the Solution Brief

The Challenge
Ransomware is no longer “a malware problem.” It’s a business disruption model built on stolen credentials, trusted tools, and lateral movement. Even strong detection stacks often alert only after attackers have already mapped the environment and identified where the leverage lives.
The practical question isn’t whether an attacker can get in. It’s whether a compromise can reach your critical applications and data. If high‑value systems remain broadly reachable once trust is compromised, ransomware retains its leverage—encryption, extortion, downtime, and cascading operational impact.
What's at stake: operational downtime, data exfiltration/extortion, regulatory exposure, recovery cost, reputational damage, and loss of customer trust.
Why Traditional Approaches Fall Short
Alerts do not automatically translate into control. Attackers can still move laterally using valid credentials and trusted tools.
Response arrives after attackers have already positioned for encryption or exfiltration.
VPNs grant network‑level reach; one compromised credential can traverse the environment.
Lateral movement becomes easy, fast, and difficult to contain.
Segmentation projects are slow and brittle: IP changes, rule sprawl, exceptions, and uneven coverage across hybrid environments.
Gaps and workarounds create invisible paths that ransomware can exploit.
Backups help recovery but don’t prevent encryption attempts, exfiltration, or operational disruption.
High downtime + extortion leverage persists, especially if attackers target backup systems too.
The Zentera Approach
Zentera assumes compromise and focuses on limiting outcomes. Instead of trusting internal reachability, Zentera enforces access boundaries around what matters most: applications and data.
Virtual Chambers (Containment)
Universal ZTNA (Verified Access)
Overlay Deployment (Speed)
Reference Architecture
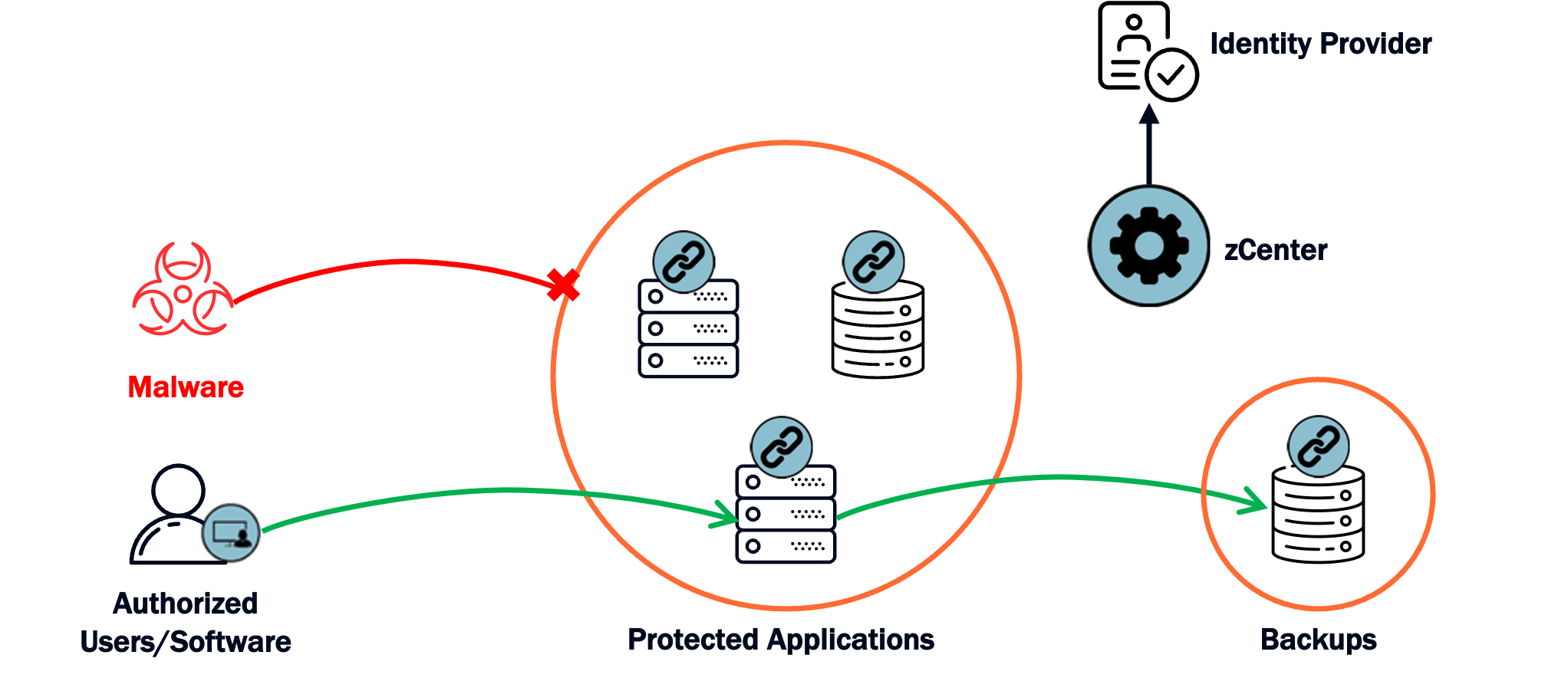
This diagram illustrates how Zentera’s enforcement model protects critical applications and data from ransomware by removing implicit reachability and enforcing identity‑ and policy‑based access to protected systems.
Identity Verification
Users authenticate through existing IdP before accessing any protected applications
Virtual Chambers
Critical applications and data are wrapped in policy‑enforced chambers that define allowed connections
ZTNA Enforcement
Only explicitly authorized users, devices, and applications can establish sessions to protected systems
Endpoint / Boundary Enforcement
Lightweight proxies enforce policy where supportable, with agentless/inline options available where required
What Changes
- Access control moves from “who is on the network” to who is authorized to this application
- Critical apps become unreachable by default, reducing discovery and lateral movement
- Ransomware incidents become containable events, not enterprise‑wide outages
What Stays the Same
- Existing IP addressing, routing, and core network architecture
- Existing security stack (EDR/SIEM/SOC) — Zentera adds enforcement, it doesn’t replace detection
- Existing applications and operational processes (no app rewrites required)
Key Capabilities
Learn normal application behavior first, then move to a tight allow-list posture for critical systems—so protection improves without breaking workflows.
See all allowed and blocked access attempts with actionable context, and export to your SIEM to support governance, compliance, and cyber insurance conversations.
Overlay architecture means rapid rollout across hybrid environments with minimal operational disruption—no IP renumbering, no network surgery, no downtime risk.
Make protected applications and data invisible to unauthorized users and compromised endpoints—scanning and "living off the land" reconnaissance yields nothing.
Create application-centric containment boundaries that prevent ransomware propagation and limit blast radius—without VLAN/firewall rule sprawl.
Enforce identity-based, least-privilege policy across remote access, on-prem access, third-party access, and machine-to-machine sessions—no implicit trust anywhere.
Implementation Details
Deployment & Operations
Outcomes & KPIs
Security
Operational
Business
Proven Results
Agility you just don't have in a traditional infrastructure
The ability to grant vendors access to specific applications without VPN has transformed how we manage third-party maintenance.
Ready to Protect Critical Assets Against Ransomware?
Talk to our architects about your specific security challenges.
Talk to an Architect
Get expert guidance on your OT security strategy
Schedule a Call 30-minute consultation