Hardening Your DMZ Against AI-Powered and Autonomous Attacks

For decades, the DMZ (demilitarized zone) has been treated as a reliable buffer between the internet and “trusted” internal systems. Expose a limited set of services, wrap them in firewalls, monitor traffic, and assume anything that makes it past the perimeter has earned a degree of trust.
 That model is breaking - fast.
That model is breaking - fast.
AI-powered and autonomous attacks don’t just exploit vulnerabilities. They exploit assumptions baked into traditional DMZ designs. And those assumptions no longer hold.
The DMZ Threat Model Was Built for a Slower Enemy
Classic DMZ architectures were designed around three implicit beliefs:
- Attackers are human-paced
- Firewall rules and signatures can be tuned fast enough
- Once traffic crosses the DMZ, it is mostly benign
AI invalidates all three.
Modern attackers increasingly use automation and AI-assisted tooling to continuously probe exposed services, test exploit chains, and adapt in real time. There is no “recon phase” followed by a clean attack window. The probing never stops.
Once a DMZ workload is compromised, the attacker doesn’t pause. Autonomous tooling immediately looks inward - mapping trust paths, testing east-west access, and identifying systems with the highest payoff.
This is why government agencies like CISA continue to warn that perimeter-only defenses and implicit trust models are failing against modern threats. The problem isn’t the DMZ itself. It’s what we assume happens after it.
How AI Changes DMZ Attacks in Practice
AI doesn’t magically invent new exploits. What it does is far more dangerous. Let’s discuss some of the most obvious challenges:
Speed and scale
AI enables continuous, high-frequency scanning of DMZ services, APIs, and exposed management interfaces. Weaknesses are found faster than human defenders can react.
Exploit chaining
Autonomous tools test combinations of misconfigurations, credentials, and vulnerabilities that defenders often consider “edge cases.” Individually low-risk issues become high-impact attack paths.
Optimized lateral movement
Once inside the DMZ, AI systems prioritize which internal connections to test first - not randomly, but based on observed responses, timing, and inferred trust relationships.
Persistence through adaptation
Blocking one technique doesn’t end the attack. It triggers the next variation. Static defenses are slowly exhausted.
Controls designed for weekly tuning and human investigation are structurally incompatible with attacks that adapt in minutes.
The takeaway is uncomfortable but necessary:
Your DMZ is no longer just a filter. It is an active attack surface under constant pressure.
Why Traditional DMZ Hardening Falls Short
Most DMZ “hardening” guidance still revolves around controls that assume attackers behave predictably.
- Static firewall rules assume known traffic patterns
- IP-based trust assumes network location equals legitimacy
- Flat internal zones assume DMZ compromise is rare
- Signature-based detection assumes yesterday’s attacks repeat tomorrow
AI punishes all of this.
Once an attacker gains a foothold in the DMZ, traditional architectures often allow broad, implicit access to internal services. That’s not a failure of firewalls - it’s a failure of trust design.
The MITRE ATT&CK framework, maintained by MITRE, consistently shows DMZ compromise as a common starting point, not an end state. Lateral movement succeeds because internal paths are trusted by default.
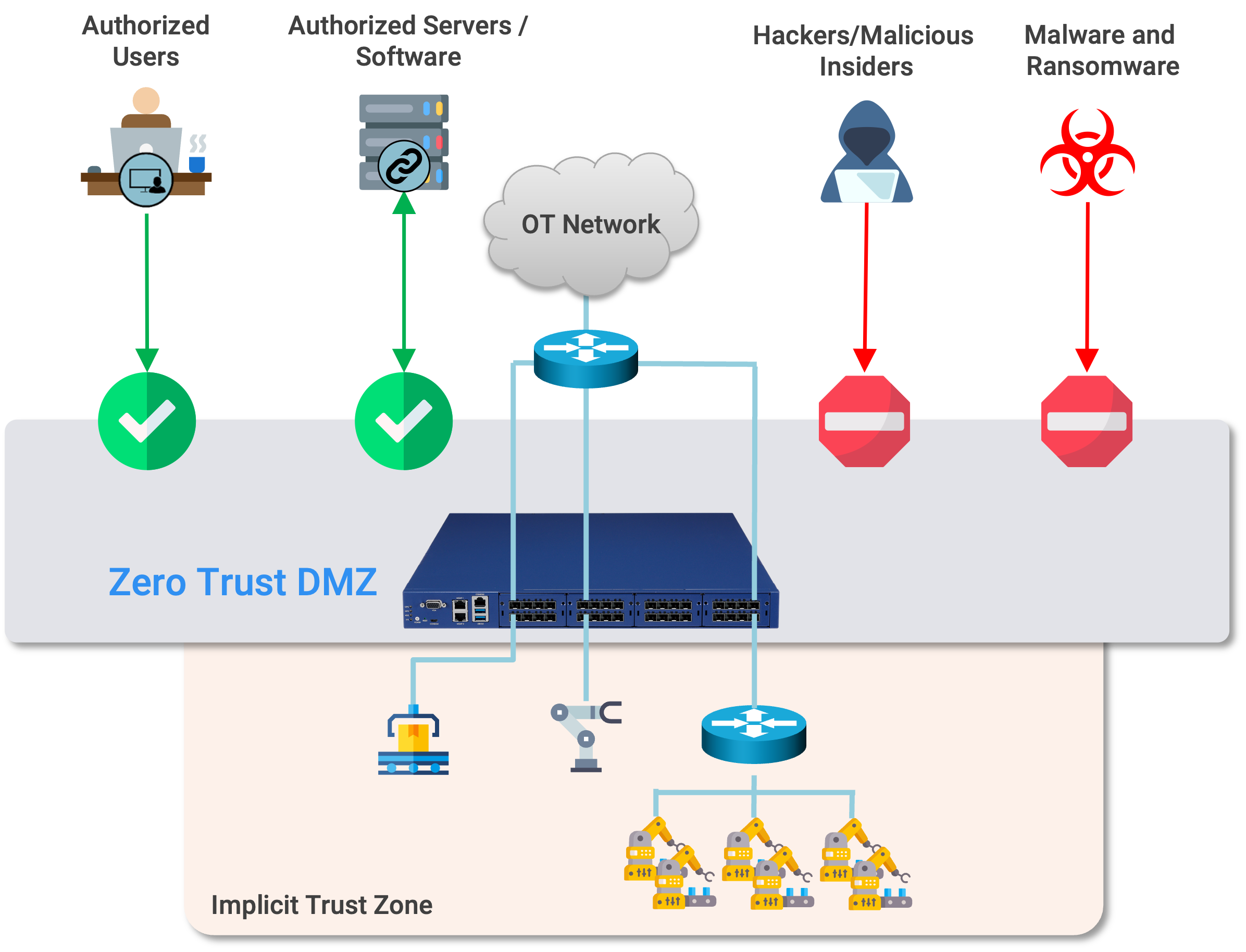
What AI-Resilient DMZ Hardening Actually Requires
Hardening a DMZ for an AI-driven threat landscape isn’t about adding more tools. It’s about removing assumptions.
-
Eliminate implicit trust beyond the DMZ
Crossing the DMZ boundary should not grant any automatic access. Every connection - even from “approved” DMZ workloads - must be explicitly authorized.
-
Enforce policy based on identity and workload context
IP addresses and subnets are weak signals in hybrid, cloud, and OT environments. Enforcement must consider what is communicating and why, not just where traffic originates.
-
Micro-isolate DMZ and internal services
Assume DMZ workloads will be compromised. Design so that compromise terminates locally instead of cascading inward.
-
Design for continuous attack, not episodic incidents
AI-driven threats don’t wait for change windows. DMZ security controls must assume constant hostile probing and enforce policy automatically.
This is where many organizations hit a gap. ZTNA solutions protect user access, but they don’t address workload-to-workload trust. Firewalls segment networks, but they don’t enforce identity-aware, least-privilege policy inside the perimeter.
A modern DMZ requires all three: segmentation, identity, and enforcement - continuously.
A Practical DMZ Hardening Checklist
If you want to pressure-test your DMZ against autonomous attacks, start here:
- Inventory every externally exposed DMZ service - no exceptions
- Remove default trust paths from DMZ to internal networks
- Enforce least-privilege access per connection, not per subnet
- Treat DMZ workloads as untrusted by default
- Measure blast radius, not just blocked attempts
If you cannot clearly explain what happens after a DMZ service is compromised, your architecture is relying on hope.
The Uncomfortable Truth About DMZ Security
AI doesn’t make DMZs obsolete. It makes weak DMZ designs dangerous.
If your DMZ security depends on attackers being slow, noisy, or human, you are already behind. The organizations that will hold up are the ones that stop treating the DMZ as a trusted corridor and start treating it as a controlled, hostile interface - enforced by policy, not assumptions.
That shift isn’t optional anymore. It’s overdue.