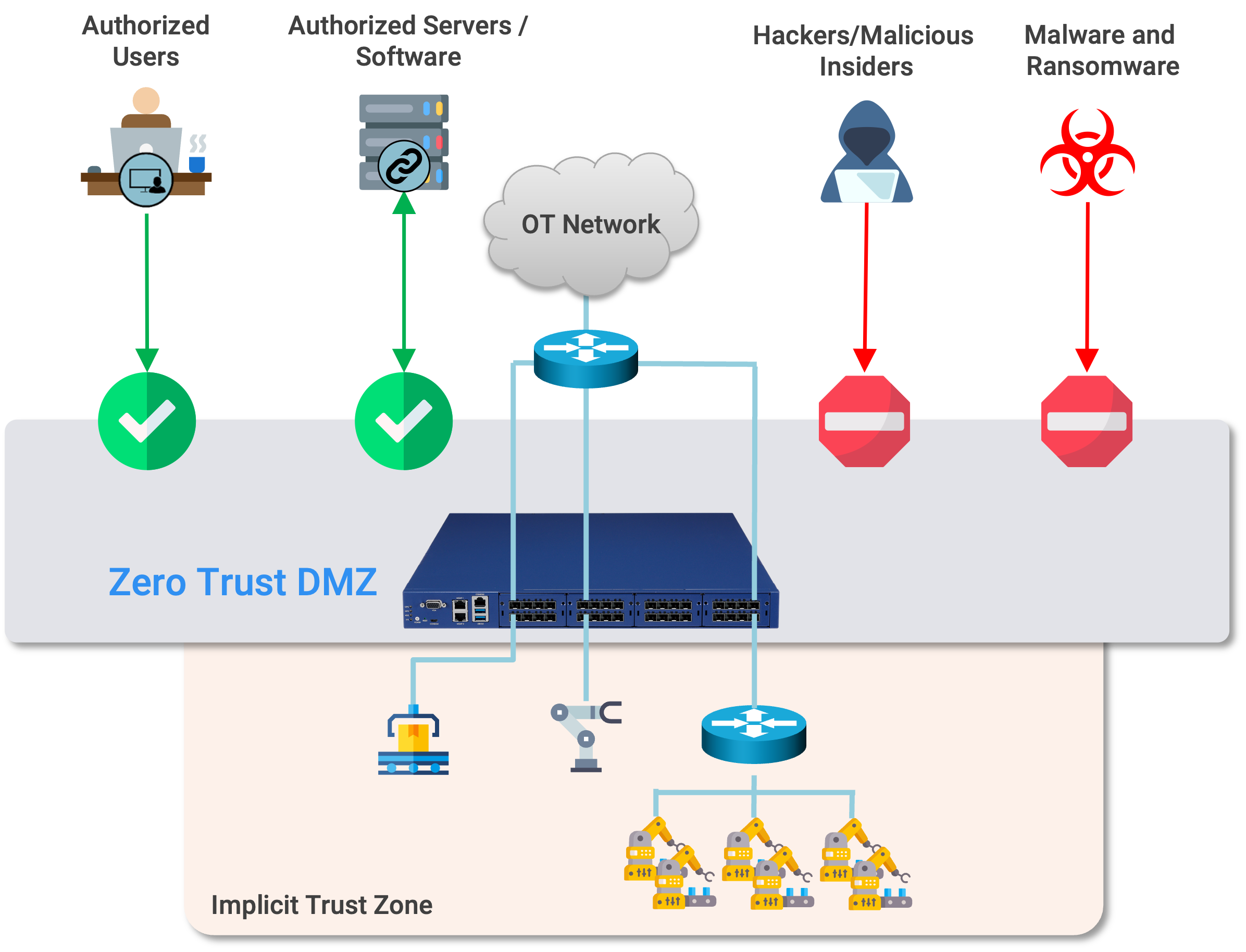
Why Zero Trust Architecture Requires Cutting Through Complexity - Not Adding More of It

The most dangerous moment in a Zero Trust journey isn't the kickoff. It's the moment 12–18 months in when leaders finally look at what they've built - and realize they've made everything more complicated, and nothing meaningfully more secure.
For years, cybersecurity teams have been pushed to "tighten" the environment: more segmentation, more firewall rules, more inspections, more identity checkpoints, more micro-perimeters around everything that moves.
 The intent is right. The outcomes are not.
The intent is right. The outcomes are not.
As digital environments expand - hybrid cloud, distributed workforces, third-party access, OT/IT convergence, and now AI-driven threats - organizations are discovering a painful truth:
You cannot secure a modern enterprise by adding complexity to an already complex network.
This is the crisis reshaping zero trust architecture. Not the philosophy itself - "never trust, always verify" remains correct - but the way organizations try to implement it.
Increasingly, security leaders are discovering that Zero Trust doesn't fail because they lack tools, budget, or expertise.
It fails because they're trying to deliver Zero Trust through a network architecture that was never designed to carry it.
And that realization forces a hard pivot: You don't reach Zero Trust by tightening the architecture you have. You reach it by cutting through the architectural constraints that are holding you back.
The Hidden Assumption That Breaks Zero Trust
Almost every major security control deployed in the last 20 years rests on one unspoken assumption:
"The network is the correct place to enforce security."
This assumption shapes everything:
- firewalls
- VLANs and subnets
- segmentation projects
- ACLs
- IP/port-based policies
- network-centric ZTNA
- east-west inspection plans
But here's the architectural flaw:
All of these controls depend on topology. And topology depends on the network beneath it. And changing networks is slow, high-risk, political, and error-prone.
This is why the simplest Zero Trust policy - "Marketing should not access R&D systems" - becomes a multi-month project involving:
- firewall teams
- network architects
- change boards
- outage windows
- dependency mapping
- and the constant fear of breaking production
All for something that should be a one-hour policy change.
And as the threat landscape evolved from perimeter breaches to lateral movement, insiders, compromised credentials, and automated reconnaissance, network-bound controls simply couldn't keep up.
The result is a painful but unavoidable conclusion:
Zero Trust architecture cannot be delivered reliably through network infrastructure that was never designed for Zero Trust.
Zero Trust Architecture: The Philosophy vs. the Reality
Search interest around zero trust architecture continues to rise - because the goals make sense:
- identity-driven access
- continuous verification
- least privilege
- microsegmentation
- reduced blast radius
- real visibility
The problem isn't the philosophy. It's the implementation - specifically, the widespread belief that Zero Trust means "do what you already do, but harder."
Most organizations attempt Zero Trust by piling more rules, more segmentation, and more control points on top of the same brittle foundation.
This produces three predictable failure modes.
1. Complexity Scales Faster Than Your Team
Every new rule must be validated against existing topology. Every microsegment becomes a project. Unexpected dependencies break production. Firewall rulebases grow far faster than they shrink.
You don't get Zero Trust. You get Zero Agility.
2. Operations Push Back - Hard
Security changes require change windows. Change windows affect availability. Availability is non-negotiable.
When operations start vetoing Zero Trust changes, programs stall or get watered down.
You don't get Zero Trust. You get Zero Momentum.
3. The Network Becomes the Bottleneck
Threats evolve fast. Identity systems evolve faster. Networks evolve almost not at all.
When Zero Trust is welded to the network, it inherits the network's worst attribute: inflexibility.
You don't get Zero Trust. You get Zero Progress.
Does This Sound Familiar?
Ask yourself:
- Does your Zero Trust model depend heavily on network topology?
- Are segmentation projects stalling due to operational risk?
- Is your firewall rulebase growing faster than governance can keep up?
- Are identity and context secondary to IPs and ports?
- Can you apply or reverse policies without a change window?
- Has your Zero Trust program made the business faster - or just made the network harder to touch?
If any answer is "yes," you're not facing a procedural problem. You're facing an architectural limit.
And architectural limits cannot be fixed with operational effort.
They require architectural solutions.
When More Control Becomes Less Security
There comes a point in every Zero Trust journey where another firewall rule, another subnet, another microsegment stops feeling like progress and starts feeling like tightening a knot that only grows more tangled.
Leaders sense it:
- "Tightening" reduces flexibility.
- New controls create new fragility.
- Mitigations introduce new failure modes.
- And every step forward adds more technical debt behind you.
This is where most Zero Trust initiatives get stuck.
Not because the team lacks talent. Not because the philosophy doesn't work. But because the architecture can no longer carry the strategy.
This is the part nobody says out loud. But every CISO knows it.
Why Zero Trust Architecture Must Break From Network-Centric Thinking
Across CISOs, OT leaders, and enterprise architects - and increasingly across major analyst frameworks - there is a growing consensus:
Zero Trust must be decoupled from the network.
Here's why.
1. Threats don't follow topology
Attackers follow identity, privilege, and software pathways - not subnets.
Network controls can't express identity, context, intent, or tool usage.
2. Business velocity outruns network change cycles
Security cannot wait weeks for change windows. Zero Trust controls must deploy in minutes.
3. Critical infrastructure can't tolerate brittle segmentation
OT systems, PLCs, production lines, legacy servers - these cannot be re-IP'd, re-zoned, or reorganized.
Zero Trust must wrap around operations, not demand operations wrap around Zero Trust.
4. Cloud and SaaS break network boundaries
Work happens everywhere. Identity is now the only durable perimeter.
The Real Shift: Zero Trust Above the Network
Organizations that are succeeding with Zero Trust are doing one thing differently: They've moved the Zero Trust control plane above the network.
That means:
- Policies based on identity + context
- Enforcement close to the asset, not the gateway
- Logical segmentation that travels with workloads
- No dependency on IP addressing or network design
- No re-IP or re-segmentation projects
- Minimal blast radius by default
- A software-defined layer independent of topology
This isn't a tactical adjustment. It's an architectural correction - the moment where the organization finally stops pulling on the rope and instead cuts straight through it.
And this correction is what allows Zero Trust to finally scale across multicloud, OT environments, hybrid networks, remote workforces, vendor access, legacy systems, and third parties. In short: everywhere your enterprise already operates.
How Leaders Should Rethink Their Zero Trust Roadmap
If your Zero Trust initiative is dragging, the next step isn't "add more controls."
It's this:
Loosen the dependencies. Decouple the architecture. Stop delivering security through infrastructure design.
Ask yourself:
- Can we express Zero Trust policy without rewriting network rules?
- Can we deploy changes fast enough to matter?
- Can we secure critical assets without reorganizing topology?
- Can we shrink blast radius without months of planning?
If the answer is no, the architecture - not the team - is the blocker.
The organizations making real Zero Trust progress aren't the ones with perfect networks. They're the ones that stopped treating network topology as their security foundation.
A Knot You Don't Have to Untie
Every enterprise eventually reaches the same realization:
Pulling harder on the old controls only tightens the knot.
Zero Trust isn't about unraveling decades of infrastructure decisions. It's about adopting a security model that doesn't depend on those decisions at all.
This is the structural shift that will define cybersecurity for the next decade: Zero Trust that operates independently of the network - because the network was never the right security control plane to begin with.
 Next Step: See How This Architectural Shift Works in Practice
Next Step: See How This Architectural Shift Works in Practice
If you're evaluating how to modernize Zero Trust without redesigning networks or slowing operations, we published a deeper analysis of the architectural shift - and how enterprises are putting it into practice.
You can read it here: Beyond the Firewall - White Paper