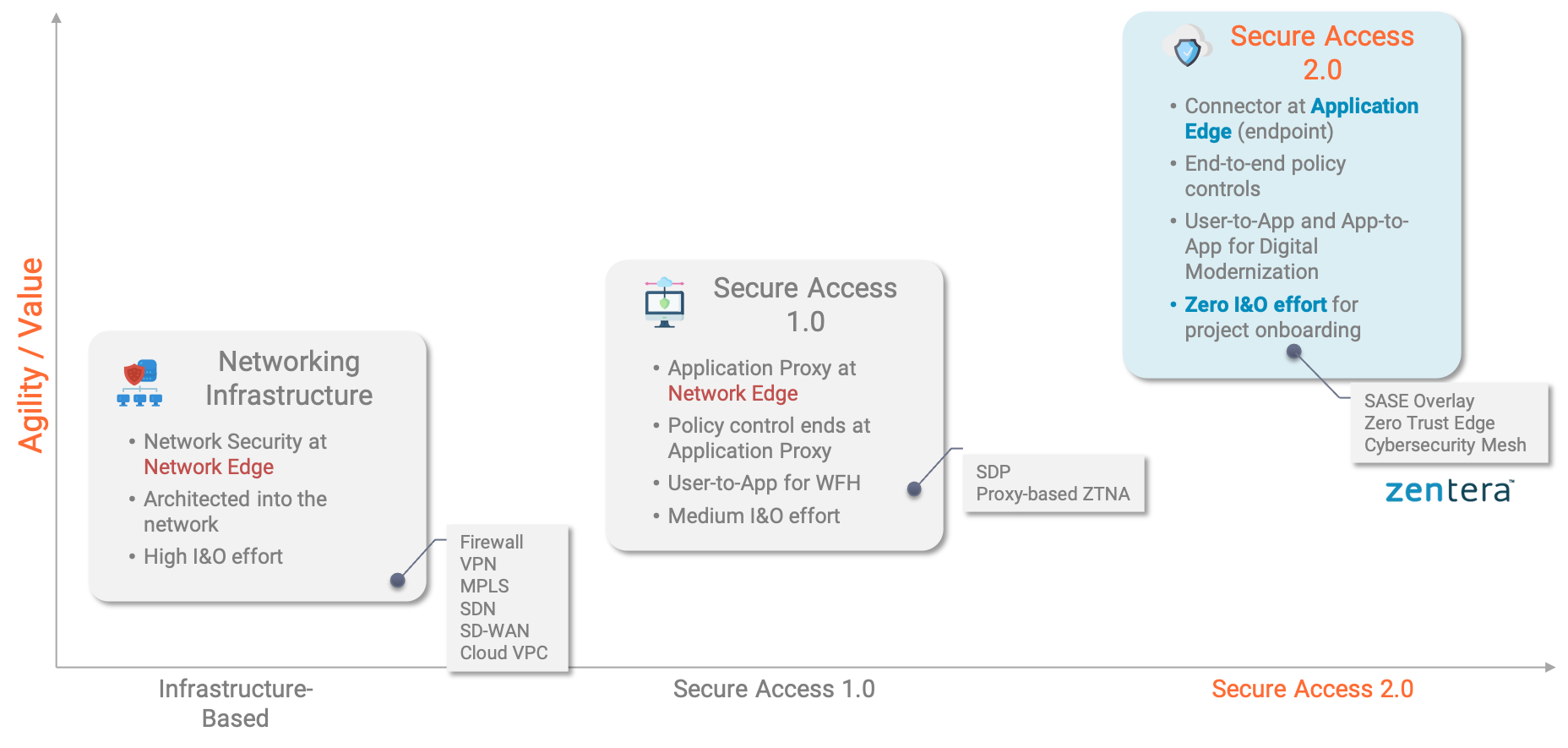
The Need for Secure Access 2.0

Have you been hearing a persistent buzzing sound recently? If you're in IT or security, it might not be your ears - it may be just the din of security vendors urging enterprises to kick old, insecure VPNs to the curb and replace them with Zero Trust Network Access (ZTNA).
Zero Trust is currently one of the hottest topics in cybersecurity. Fueled by near-daily reports of major ransomware attacks and fanned by an Executive Order from the White House, Zero Trust marketing has reached a fever pitch in 2021. ZTNA has been anointed as the new, secure version of VPN, but if you think what the major vendors have introduced so far is lacking, you're not wrong.
Let's call the initial vendor implementations of ZTNA "Secure Access 1.0." Secure Access 1.0 includes many popular solutions, such as software defined perimeters (SDP). A hallmark of a Secure Access 1.0 implementation is a secure access client, connecting to a ZTNA gateway deployed at the enterprise edge – sometimes integrated with the firewall. The gateway opens for authenticated users, allowing the user to access the application behind the gateway. It’s simple to understand, yet this model delivers only partial Zero Trust.
To see why, we can use the hotel model of enterprise security. You wouldn't stay in a hotel without locks on the guestroom doors, would you?

The Hotel Model of Enterprise Security
Think of your enterprise as a busy hotel: guestrooms (servers and applications) are divided among different floors (subnets and VLANs). The lobby (corporate DMZ) is a common area through which guests (packets) are constantly coming and going. Arriving guests are greeted by the front desk and hotel security personnel (the corporate firewall), and are given access to their rooms after checking in.
A VPN is fundamentally a secure transport service, not a secure access control service – in our analogy, the VPN is like a hotel shuttle that brings guests to the front door, and that’s it. Once the VPN connects the network, it doesn’t control what jobs or tools on a user client machine can or cannot access which applications behind the enterprise firewall, and that's the problem - practically anybody could hop on the shuttle to our hotel, leaving the job of weeding out unsavory characters to the overworked front desk check-in.
Secure Access 1.0 solutions typically replace the standard VPN with enhanced authentication before access is established. Authenticated traffic is allowed, and some security filtering is performed at the gateway. Essentially, a Secure Access 1.0 solution verifies who the guests are before they even get on the shuttle, with a few security checks at the front desk.
Problem solved? Not exactly.
After the access terminates at the ZTNA 1.0 gateway, who takes responsibility for ensuring the packet can only travel to the destination resource? (hint: no one) Worse, the packet may not even be able to get to the resource, which may be behind layers of firewalls. It means the Secure Access 1.0 "solution" didn't actually save any infrastructure effort, especially if the company like many security-sensitive enterprises, is already partially segmented for protection.
But there's another problem. Once a user has successfully accessed a machine behind the enterprise firewall, how can you stop this person from hopping laterally to other machines that may not be protected against external access? In our hotel example, how to stop a person from sneaking out of their room to search for other unlocked rooms? Secure Access 1.0 assumed the hotel is secure, trusts the guests not to roam, and doesn’t lock doors to the rooms, either.
You see, most Secure Access 1.0 solutions are designed with web application access in mind. With this model, extra security measures are out of scope; once the access can reach the web service, Secure Access 1.0’s job is done. But to serve as a true VPN replacement, ZTNA needs to be able to support more complex accesses models – user-to-app and app-to-app – such as ssh, as well as standard TCP/IP client/server applications. ZTNA also needs to control access end-to-end – and be able to stop it at the other end. If you give a remote user ssh access to a machine, you're going to want to be sure that the user doesn't abuse that privilege to move laterally within your organization to access other resources.
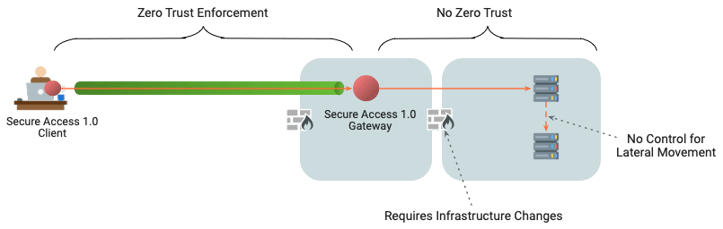 Secure Access 1.0 – Partial Zero Trust
Secure Access 1.0 – Partial Zero Trust
Enter Secure Access 2.0
The Secure Access 2.0 paradigm follows the same basic principles introduced by Secure Access 1.0, namely to authenticate users and endpoints, and to authorize every transaction. Secure Access 2.0 expands on this model by adding the following key requirements:
- Control accesses from end-to-end
- Control the potential for lateral migration
Controlling access from end-to-end means from the source, all the way to the destination machine – and not anywhere else.
At Zentera, we address this by providing an agent both at the source and the destination, and by routing traffic through an overlay network with cryptographic protection for data in transit. As trust in each transaction is built through authentication and authorization checks, this means that overlay packet traffic can be trusted and are tamper-free when they are presented to the destination application.
Lateral migration is controlled by fusing Zero Trust Network Access with micro-segmentation controls, giving administrators the confidence that remote access can't be abused to inject malware or probe the rest of the network.
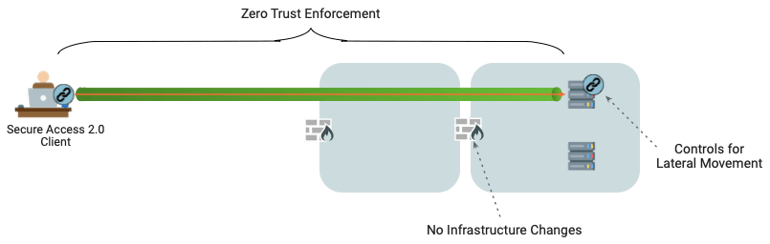 Secure Access 2.0 – Full Zero Trust
Secure Access 2.0 – Full Zero Trust
Back to our hotel example, with Secure Access 2.0, guests check in with a room key, prior to boarding the hotel shuttle, and are escorted directly to their rooms. Rooms are locked, exits are continuously monitored, and any unauthorized attempt to leave sets off alarms.
Finally, because our Secure Access 2.0 is built on an overlay network, it’s completely decoupled from the existing network infrastructure. There’s no need to open any ports or expose the gateway machines themselves for inbound access.
The Takeaway
Secure access is critical for our complex, cloud-enabled futures, and pushing the security demarcation to the endpoint, with Secure Access 2.0, is the way to achieve Zero Trust security and reduce or even eliminate I&O challenges – all at the same time. With technologies like 5G disrupting how we think of networks, it's even more important to adopt solutions supporting this technical approach now, to avoid delays and expensive re-engineering later when the complexity level rises to necessitate it.