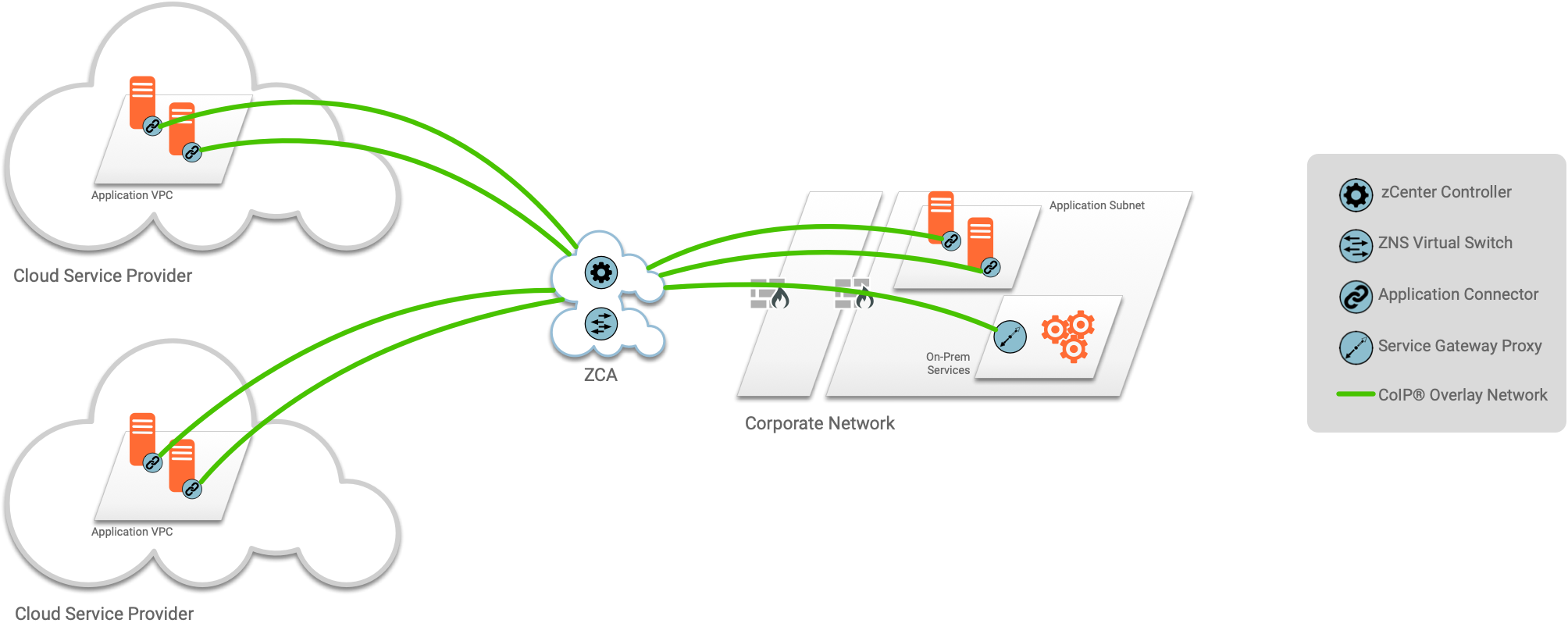
The Solution: Connect Applications, Not Networks
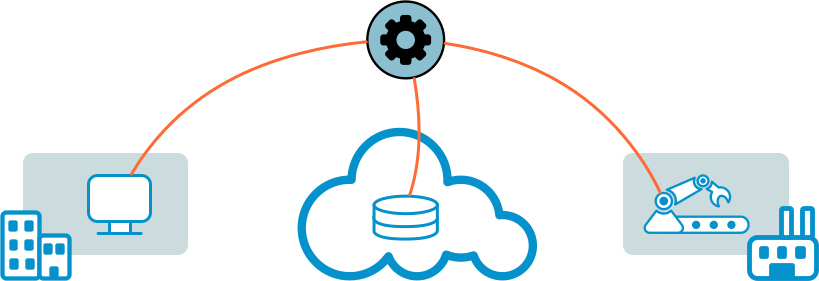
CoIP Platform offers an alternative methodology that scales elegantly in a multi-cloud and hybrid environment. Instead of creating a gigantic unified IP network, CoIP Platform enables you to securely connect applications across disconnected network domains. This decouples the various infrastructure environments and network silos, allowing each one to be managed and run independently of the others.
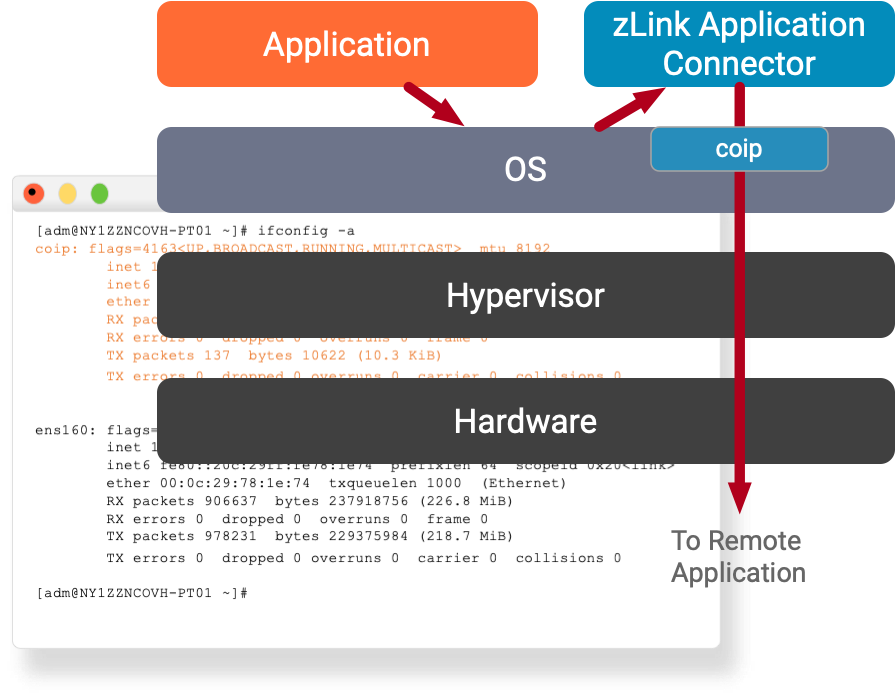
The CoIP AppLink session tunnel works as an application connector — it connects applications in any environment, without requiring support from the underlying network infrastructure, by creating a virtual interface for secure overlay communications.
Built on the principles of Zero Trust, CoIP Platform authenticates users, endpoints, applications, and services using policy-based access connectivity and strong trust factors. Deploying as software, it secures application access connectivity without touching existing corporate VPNs, routers, or firewalls.
Application teams can set up and manage their own application-centric access , without having to file tickets to the corporate IT infrastructure team to create IP network-level connectivity.