Knowledge Base
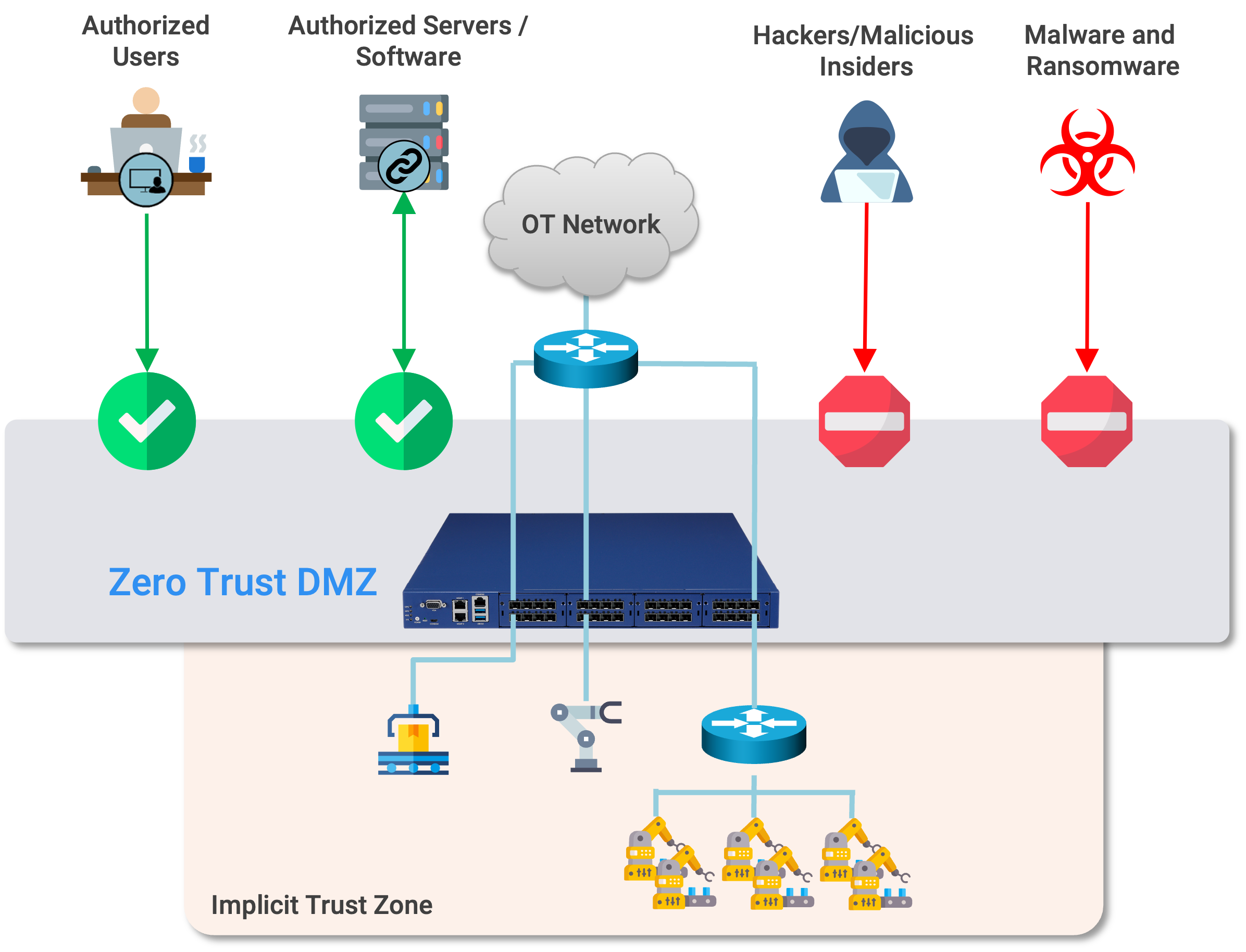
What is a Zero Trust DMZ for OT?
This article is part of our series on Zero Trust. For more information on Zero Trust, check out Zero Trust, Explained. What is a network DMZ? A demilitarized zone, or "DMZ", is one of the workhorses of network security architecture. A DMZ refers to ...
Read