White Paper
Simplifying Cloud Security with Zero Trust and SASE as a Service
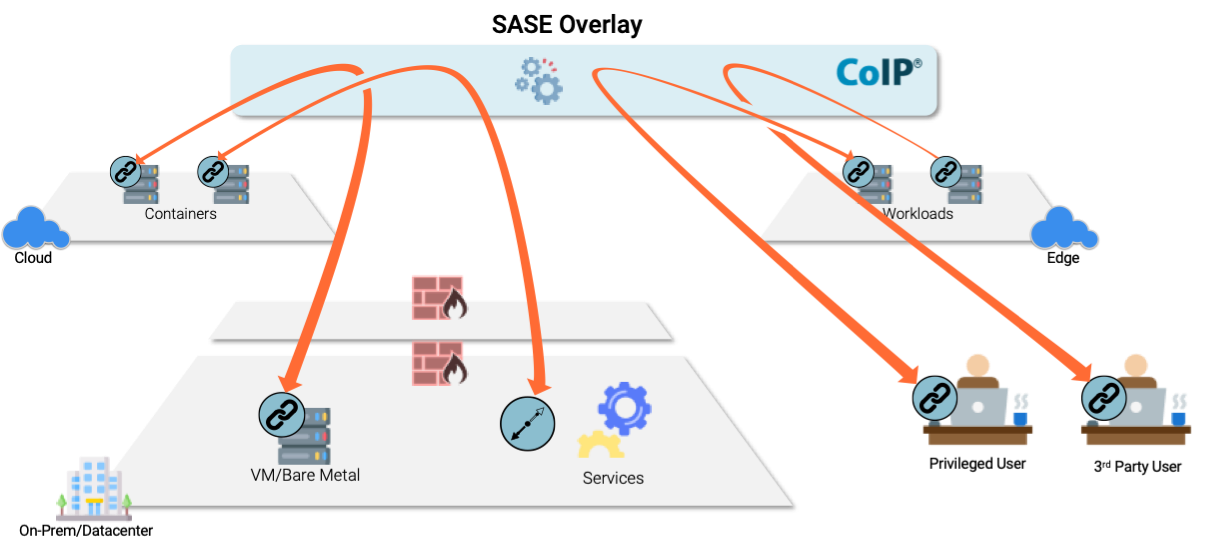
Migrating to the cloud is easy... until it isn't, anymore. Download this white paper to CoIP Access Platform to understand the pitfalls that come with cloud and multi-cloud scaling, and how to address them with SASE overlays and Zero Trust.